
Below we have hand picked some tools below which we believe will be useful for your hunt. All of the them together should be enough to help you gather large amounts of data, enough to hopefully find at least one bug!

Burp Suite
Burp Suite by PortSwigger is used for monitoring requests from your computer & websites. PortSwigger offer a free community edition and also a PRO edition, which also gives you access to extensions. The community edition works fine for those just starting out in bug bounties however the extensions that come with PRO definitely do make your life a lot easier. If you can upgrade, it's recommended. This is the most used tool when conducting website security testing.
An alternative to Burp Suite is Fiddler by Telerik. Fiddler does everything Burp can do and even has extensions.
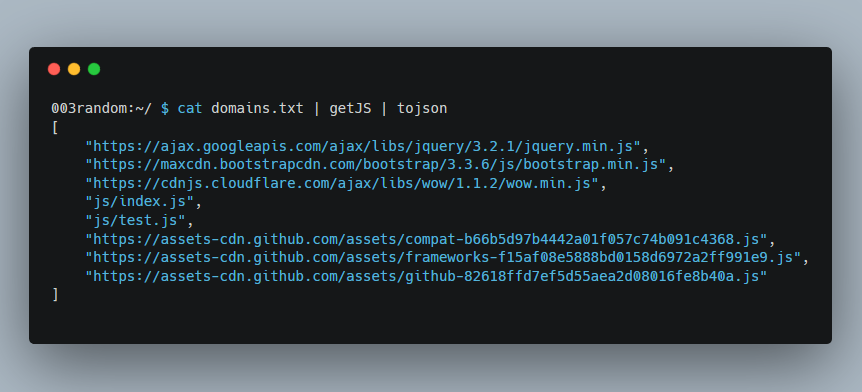
GetJS by 003random
GetJS will take a list of domains and extract any .js files found on each domain. This is useful if you want to sort through lots of .js files for new urls/endpoints on a mass scale.
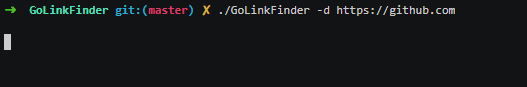
GoLinkFinder by 0xsha
GoLinkFinder will extract URLs and endpoints from JS files from a list of urls you provide.
getallurls
getallurls (gau) fetches known URLs from AlienVault's Open Threat Exchange, the Wayback Machine, and Common Crawl for any given domain. Inspired by Tomnomnom's waybackurls.
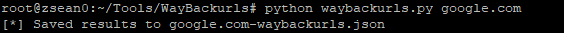
WayBackUrls by mhmdiaa
WayBackUrls will extract urls archived by WayBackMachine for the domain you input. An alternative in GO is TomNomNom's WayBackUrls
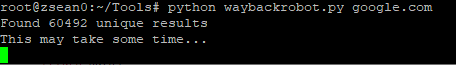
WayBackRobots by mhmdiaa
WayBackRobots — Lots of companies list endpoints in /robots.txt and this changes overtime. Who's got it all archived? WayBackMachine! WayBackRobots will extract as much robots.txt information as possible from years ago for your chosen domain. Very useful for finding old endpoints which may still work!
MassDNS by blechschmidt
MassDNS is a simple high-performance DNS stub resolver targeting those who seek to resolve a massive amount of domain names in the order of millions or even billions. Without special configuration, MassDNS is capable of resolving over 350,000 names per second using publicly available resolvers.
Alternative subdomain scanners
There are a lot of alternative subdomain scanners such as:
Subdomain Discovery Services
There are a variety of services available to provide you with recon data. Some of the data is free and some require a membership, although if you follow them each on twitter they often post free trials to test their services!
- Spyse Cybersecurity Search Engine Membership
- ProjectDiscovery.io
Make sure to check out Chaos which is a collection of internet wide asset data. Free - https://recon.dev Membership
FFuF
Fuzz Faster U Fool! Let the GitHub repo do the talking: FFuF. An alternative to FFuF is wfuzz - WFUZZ
codingo has a great video on How to master FFUF for Bug bounties and Pen testing and InsiderPHD also has a video titled, How to use ffuf - Hacker toolbox. Be sure to check both out so you can learn how to use FFuF to it's true potential (because trust me, you want to!).
——
Other helpful tools / scripts
- XSSHunter: XSSHunter
- SQLMap: http://sqlmap.org/
- XXEInjector: XXEinjector
- SSRFDetector: ssrfDetector
- GitTools: GitTools
- gitallsecrets: git-all-secrets
- nmap: https://nmap.org/
- RaceTheWeb: Race The Web
- CORStest: CORStest
- EyeWitness: EyeWitness
- parameth: parameth

 Getting started
Getting started Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Test your knowledge
Test your knowledge Free Web Application Challenges
Free Web Application Challenges Guides for your hunts
Guides for your hunts  ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Useful Resources
Useful Resources  Disclosed HackerOne Reports
Disclosed HackerOne Reports  Our community
Our community Endorsed Members
Endorsed Members Hackevents
Hackevents  Member Articles
Member Articles