FirstBlood-#109 — An new user account can bypass security and view all appointment data
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-10, xnl-h4ck3r Level 4
reported:
**NOTE: THIS WAS INCORPORATED INTO REPORT #106 BECAUSE I WANTED TO MAKE A BETTER INITIAL REPORT :)
Summary
An authoriation vulnerability exists that allows a new user to access pateinet appointment PII data.
When logged in as a new account, the user cannot look at a pateients appointment on /drpanel/index.php, and is given the message "You are not authorised to view this. Consult your medical administrator.". A user can bypass this security and call endpoint /drpanel/drapi/query.php directly and access the data.
An IDOR exists on the parameter aptid of this endpoint.
Steps to Reproduce
- Log in as a new user, and observe the message below:
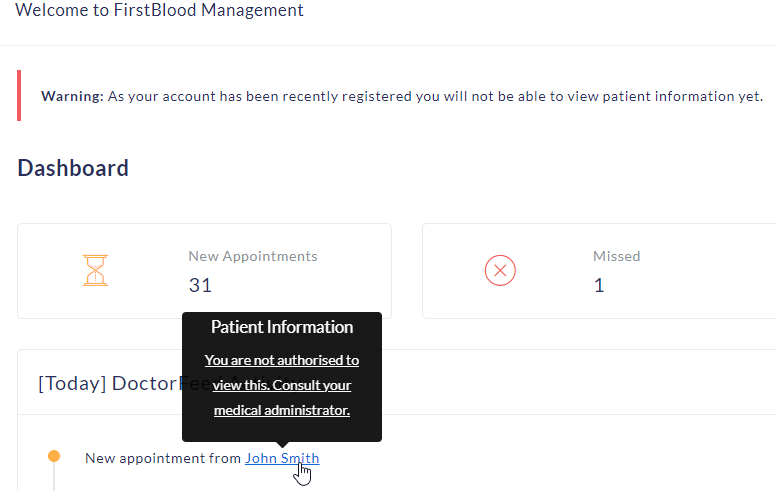
- To bypass this security, send a GET request to
/drpanel/drapi/query.php with the cookies of the logged in user, and query parameter of aptid=56910619 for example.
- Observe the response with data of a patients appointment:
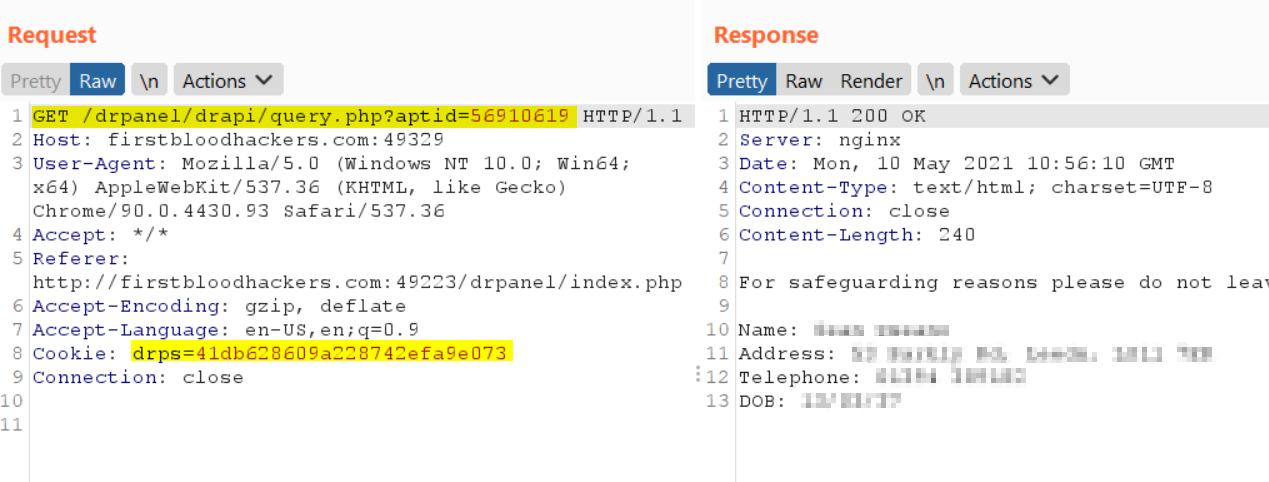
NOTE: An IDOR exists that means the appt value is 5691???? where ???? is enumerated by adding 137 to the previous value each time.
Impact
Authorisation controls can be bypassed allowed new users access to patient appointment PII data
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /drpanel/drapi/query.php
Parameter: appt
Payload: aptid=56910619
FirstBlood ID: 11
Vulnerability Type: Application/Business Logic
Administrator endpoints can be accessed by non privileged doctor accounts which reveals sensitive patient information.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
