Description
Hello Sean,
I've recently found out that Patient's can modify their information without authorization on /manageappointment.php
However, I just found out that the email and message of any other users can also be changed using an IDOR on the aptID of the patients.
In the other report I linked above there was no need for the IDOR on aptid and that was considered as an application logic bug. however, in this case, we are making use of an IDOR on the aptid parameter.
Steps to reproduce
- First of all, you need to make an appointment on the
/book-appointment.html endpoint as an unauthenticated user, an example of such is shown below:

- After doing so you will be given an appointment ID so that later on you can use it to visit your appointment details and to modify or cancel them.

- Now open the
/yourappointments.php endpoint and enter the appointment id that you got from the previous step.
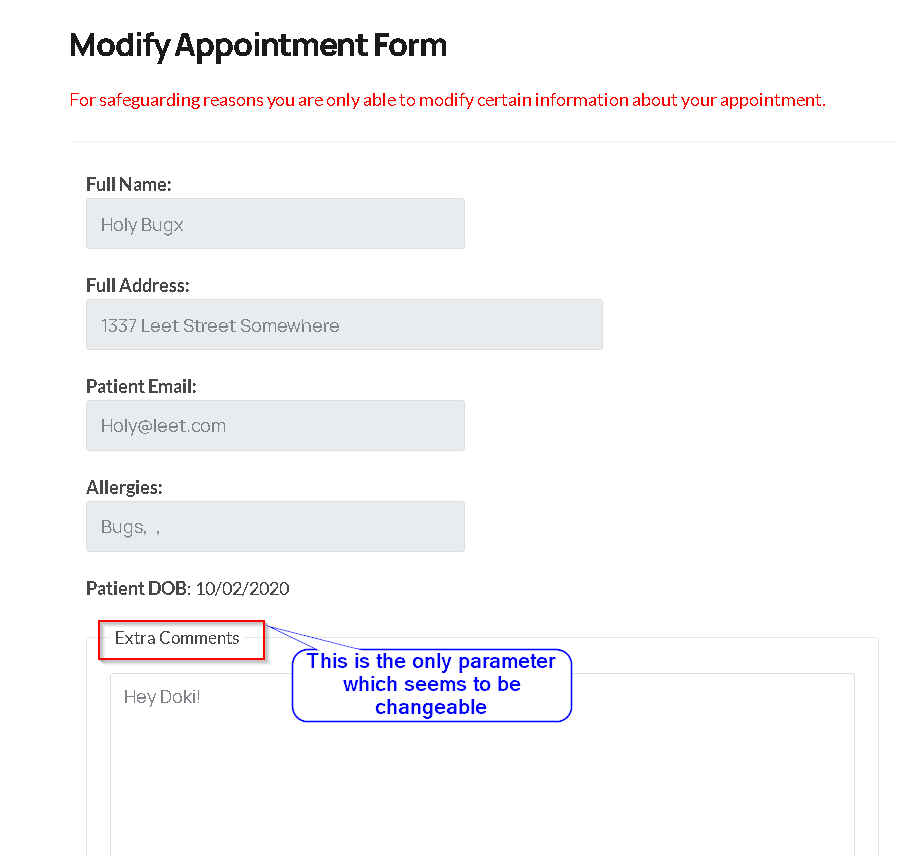
- Intercept the request to "Modify Appointment" and make the following changes, and then send the request:

- If you now, go to the doctor's panel and open "Cancelled Appointments", you can see the message that "Sean Zseano" had left before is now changed with what we just set, meaning that his
aptID was used and his message is now changed.

-
As explained above the aptID of other users can be used to change their email and message.
-
In the proof of concept I shown above I changed the message of another user, Note that the email address of any user can be changed as well using the same IDOR.
Modifying Email address of other users
- Victim's current information:

An attacker can make his appointment as shown before, and intercept the request to "Modify Appointment" on his side:

Here is the example HTTP request the attacker has:

- Attacker adds the
doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9 cookie.
- Attacker adds the
email parameter with the email address he wants.
- Attacker changes his
appointmentID with the victim's aptid
I explained how an attacker can find the aptid of other users in this report. also, it's good to note there is no need for the attacker to be a "new doctor" same as the report linked above, the attacker can blindly Brute-Force the last 4 digits and the email address of users with the valid aptid will change.
Here is the new victim's account information after the attack:

- You can notice that the
email of the victim is now changed to the attacker's provided email address.
Notes
- If the attacker only wants to change the
message of others, there is no need for the doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9 cookie.
- There is absolutely no need for an attacker to know the
aptid of other users, he can simply Brute-Force them blindly as I showed before on this report.
Impact
- Unauthorized modification of other user's email addresses and messages using an IDOR.
Please let me know if you need further assistance.
Best Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 







