FirstBlood-#511 — Can update any users password if know the username, and therefore takeover any account and get Admin access
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-25, xnl-h4ck3r Level 4
reported:
Summary
An attacker is able to reset the password (without being authenticated themselves) of any user on the site as long as they know the username. It was known from Version 1 that the admin user was drAdmin, and therefore an attacker can also reset that users password and gain admin access.
The following commented out code can be found in the /drpanel endpoint if a user is logged in:
/* to do
function editpassword(username) {
var xhr = new XMLHttpRequest();
xhr.open("POST", '', true);
xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
xhr.onreadystatechange = function() {
if (this.readyState === XMLHttpRequest.DONE && this.status === 200) {
alert(this.responseText);
} else {
}
}
xhr.send();
} */
This highlights the feature that is in development that can be used to reset passwords.
Steps to reproduce
-
Make a POST request to /drpanel/drapi/editpassword.php with a Content-Type of application/x-www-form-urlencoded and the username paramater in the body of these users password you want to reset, e.g. username=drAdmin
-
Send the request and observe the response that shows the updated password:

-
Log in using the username and new password.
-
Using the excample of username drAdmin, observe that we now have admin access by being able to veiw the details of appointments on /drpanel:
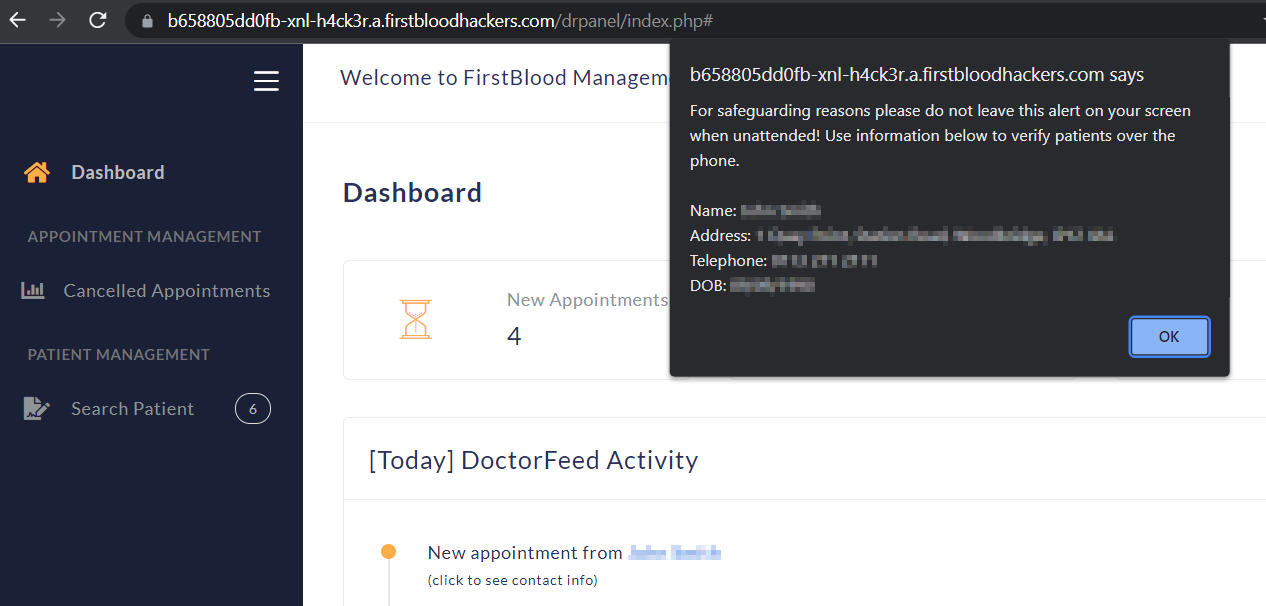
Impact
An attacker can take over any users account (without being authenticated) if they know the username, including admin users and gain access to all patient PII details.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /drpanel/drapi/editpassword.php
This report contains multiple vulnerabilities:
FirstBlood ID: 27
Vulnerability Type: Application/Business Logic
It is possible to edit the admins password (dradmin) from /drapi/editpassword as it's only looking for the username. Usernames can be enumerated when logging in as trying 'drAdmin' results in a different error. The username can also be found from FirstBlood v1.
FirstBlood ID: 28
Vulnerability Type: Auth issues
The endpoint /drapi/editpassword can actually be accessed unauthenticated.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
