Description
Hello Sean,
I found out that Unauthorized users can query for every patient they want using the /drpanel/drapi/qp.php endpoint, this leads to unauthorized access to the user's PII such as name, telephone, address, DOB.
Steps to reproduce
I found out that doctors can query for their patients using the /drpanel/drapi/qp.php endpoint, when they query for a patient's name they will be given his information that is used to verify a patient over the phone.
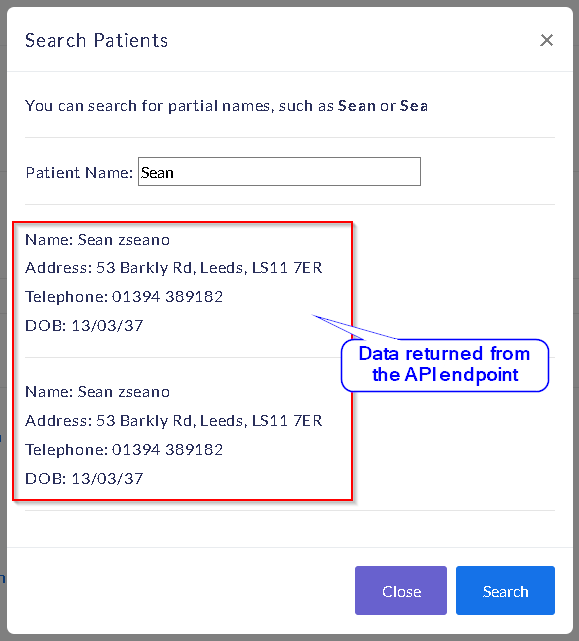
If a doctor query for a patient using the "Search Patient" button in their panel, a POST request is sent to the /drpanel/drapi/qp.php API endpoint, and the data is returned in their portal:
Here is the POST request being made to the server:
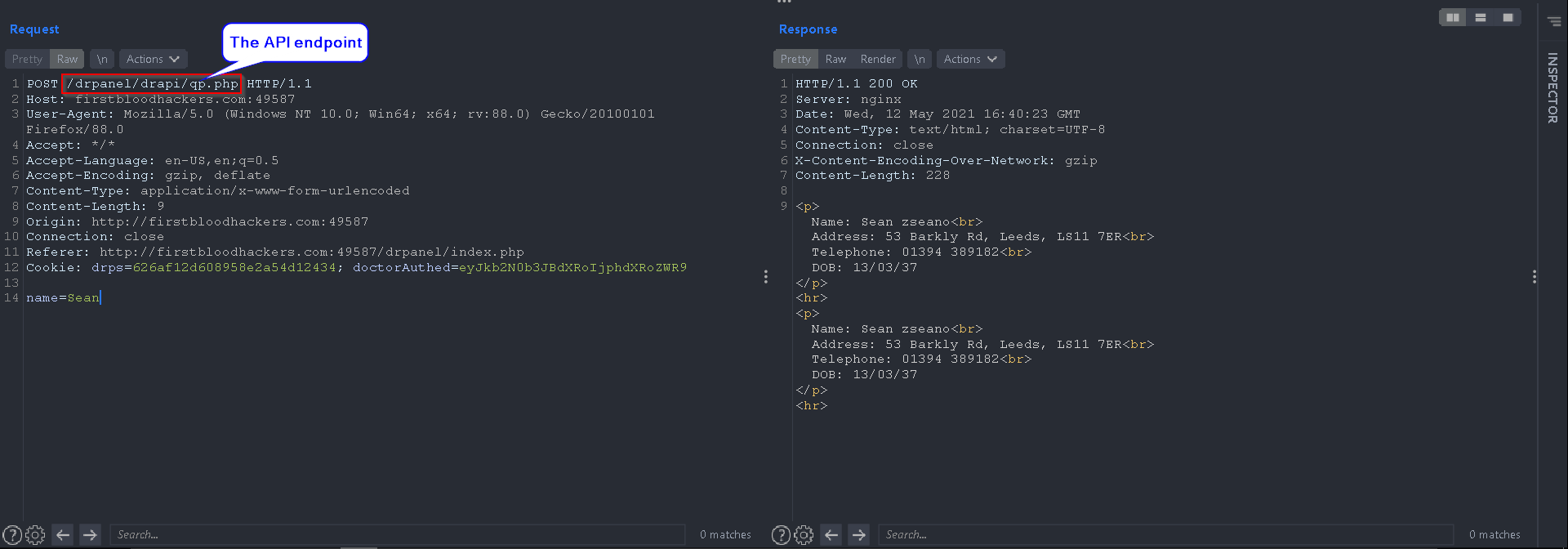
I found out that changing the POST request to GET will result in the following URL endpoint, which can be used to fetch the data of patients:
http://firstbloodhackers.com/drpanel/drapi/qp.php?name=Sean
However, any unauthorized user can use this API endpoint to query for patient names and their PII.
An attacker doesn't need to know the name of the patients to query for. if the name parameter is empty all of the patient's data returns:

Impact
Critical PII Leakage
Kind Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


 Report Feedback
Report Feedback