Dear FirstBlood security team, I found a vulnerability on your service.
I hope this report will help you.
Summary
In Modify appointment page, we can change our booked appointment.
Because of no protection against XSS, the malicious user can perform Stored XSS and it can lead to account takeover.
Vulnerability Description(PoC)
First of all, /manageappointment.php endpoint has a JS snippet like below:
<script>
var msg = '<user message is filled here>';
$(document).ready(function () {
document.getElementById("message").value = msg;
});
</script>
var msg reflects user's message param value so if we input message=hoge, then it becomes var msg = 'hoge';.
There seems no sanitization, we can easily perform XSS by entering msg='*alert(document.cookie);//.
This is the evidence of it.
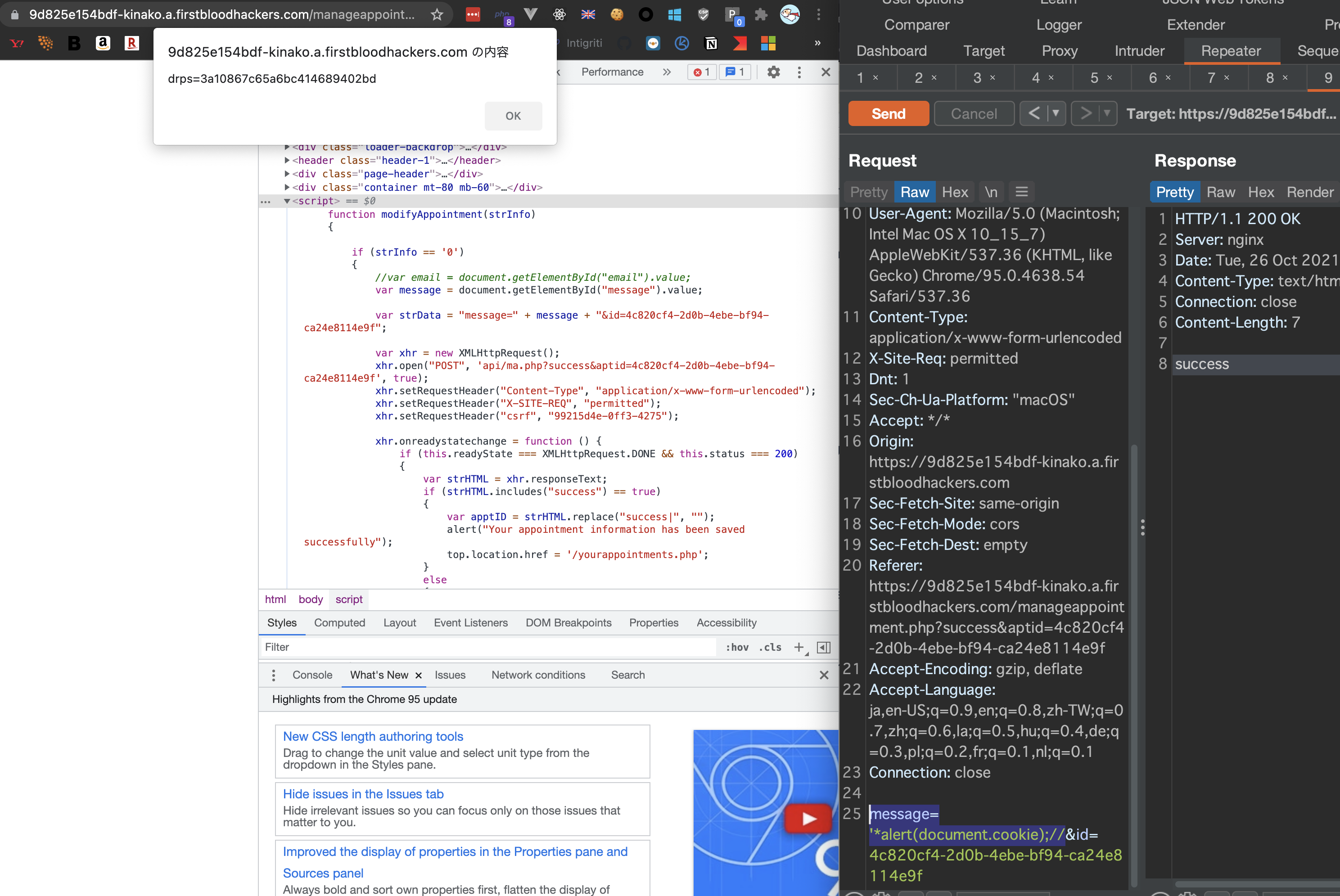
HTML source.

I thought this is so-called "self-XSS".
In conclusion, this is not self-XSS.
I tried to find the way of making victim modify their message value to XSS payload, but so far I don't find such a way.
After that, I noticed this page does not require any session or login process.
This means that everyone who knows this URL like https://9d825e154bdf-kinako.a.firstbloodhackers.com/manageappointment.php?success&aptid=<aptid> can see others' modify appointment page.
(Generally speaking, edit page like this restricts to see other users' edit even though they know edit page URL but firstblood v2 modify appointment page doesn't!)
So if the attacker is successful in making victim access to malicious modify appointment page, then they can perform XSS without any other process.
Impact
- firstblood v2 still does not have HttpOnly flag in Cookie so the attacker can steal session cookie relatively easily
- Phishing
Regards,
kinako
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
