FirstBlood-#56 — Stored XSS on /drpanel/drapi/query.php?aptid=<ID>
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-09, rintox Level 3 reported:
Summary
There's a Stored XSS when booking an appointment. When a Doctor wants to see the contact information of a client, with the right payload, the first name parameter is vulnerable to a SXSS attack.
Steps to reproduce
- Go to the endpoint /book-appointment.html
- In the first name field, insert the following payload: Rintox <svg/onmouseenter="confirm`1`">
- Now as the logged-in Doctor, visit the main dashboard and notice the appointment
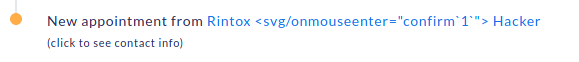
- When clicking on the name, the application will make a request, grab that request from burp.
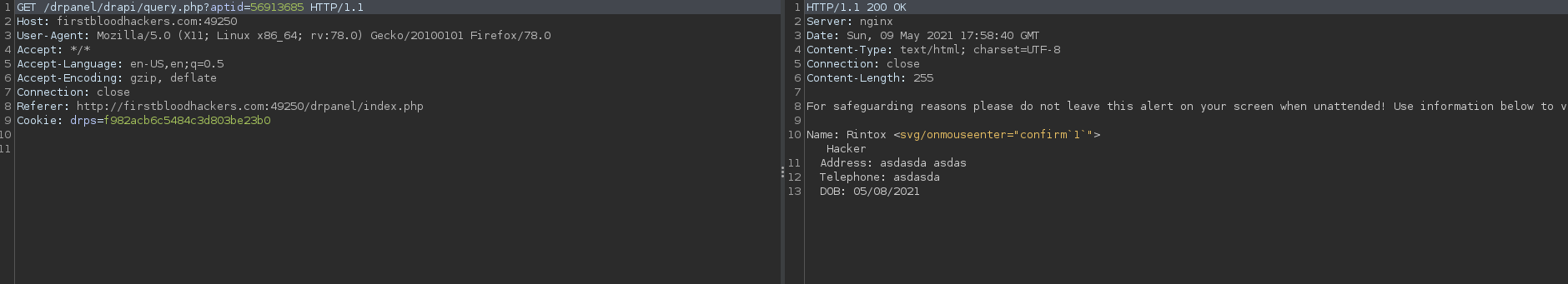
- You can notice the response has a content-type of text/html.
- Now visit that URL and hover your mouse over the end of the name (in this case Rintox) and the XSS will execute
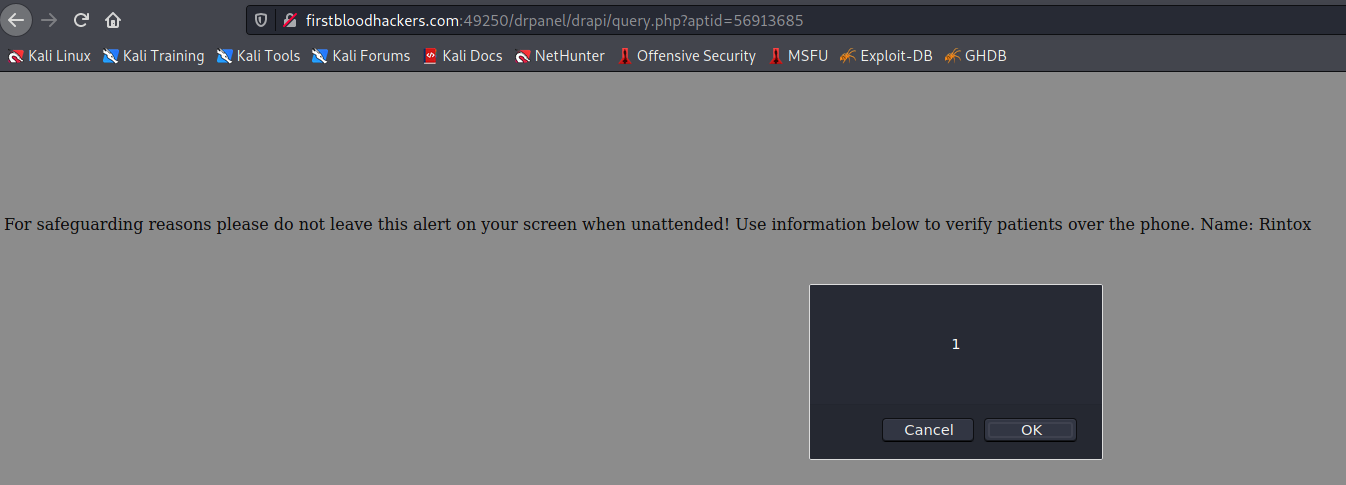
Impact
The Stored XSS will affect all logged-in Doctors including admins, that when visiting the URL of the client information, the malicious JS code will execute.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /book-appointment.html
Parameter: fname
Payload: Rintox <svg/onmouseenter="confirm`1`">
FirstBlood ID: 10
Vulnerability Type: Stored XSS
When creating an appointment, it is possible to get stored XSS /drapi/query.php via the patients name
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

