FirstBlood-#788 — Unexpected registered users
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-28, axe Level 4
reported:
Summary
-
many thanks to my friend for giving me the right direction.
-
I am really thankful to zseano, for organizing this bounty event, which made me learn a lot.
-
He has taught me the importance of reading the rules and the groundbreaking thinking and grasp of detail needed to dig for loopholes!!!!
-
have been very excited because of this discovery.
Steps
-
At first I had a guess at the end of registering users. I found out that when I entered the drAdmin user and the 1111 invitation code. This is the administrator account and you are not allowed access.This lets us know that thedrAdminuser exists and still hasadministrator` privileges.

-
During this time I also read the full report disclosed by v1. I know this invite code was found in v1 through a google search.

-
But after a long time of testing I didn't test successfully. Until today my friend gave me the right direction, he told me to read the rules of v2 carefully
-
After I carefully read the rules of v2, I found a lot of fonts are shown in bold.

-
After careful observation, I found that the test character is different from the others. Normally, the boldness of the font is testing together with boldness. But this test is different. It is bolded separately. So I tested this test as a username and invitation code together. I didn't expect it to work! I'm so happy that my long-standing login problem is finally solved!
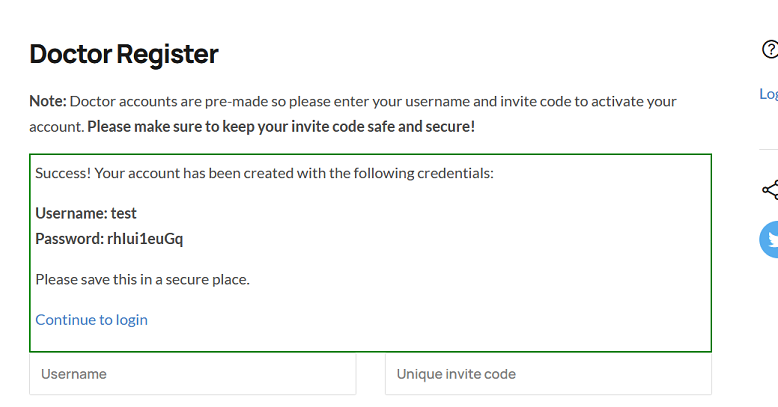
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /register.php
Parameter: inviteCode
Payload: NA
FirstBlood ID: 24
Vulnerability Type: Auth issues
The old invite code was deleted but when testing FirstBlood v2 the developers accidentally left the test code working.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges BugBountyHunter Membership
BugBountyHunter Membership ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


